Author: Cybernoz
An Android malware app called SpyLend has been downloaded over 100,000 times from Google Play, where it masqueraded as a…
Chinese cybersecurity entities have accused the U.S. National Security Agency (NSA) of orchestrating a cyberattack on Northwestern Polytechnical University, a…
A significant vulnerability in Sitevision CMS, versions 10.3.1 and earlier, has been identified, allowing attackers to extract private keys used…
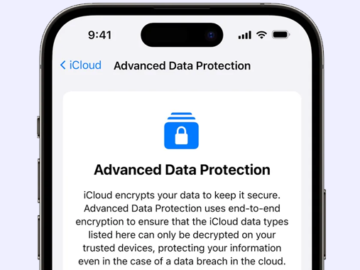
Apple has withdrawn from providing its UK smartphone and computer users with encrypted cloud storage following a secret government order…
In a recent development, the SPAWNCHIMERA malware family has been identified exploiting the buffer overflow vulnerability CVE-2025-0282 in Ivanti Connect…
Feb 21, 2025Ravie LakshmananSurveillance / Content Monitoring An analysis of a data leak from a Chinese cybersecurity company TopSec has…
Apple will no longer offer iCloud end-to-end encryption in the United Kingdom after the government requested a backdoor to access…
Healthcare is one of the sectors that has the most sensitive information about us. At the same time it’s one…
Feb 21, 2025Ravie LakshmananData Protection / Encryption Apple is removing its Advanced Data Protection (ADP) feature for iCloud from the…
Grant Thornton has issued a forensic 66-page report relating to a failed Oracle Fusion enterprise resource planning (ERP) implementation at…
Cryptocurrency exchange Bybit revealed today that an unknown attacker stole over $1.46 billion worth of cryptocurrency from one of its…
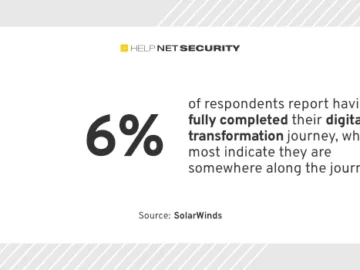
For most public sector organizations, digital transformation is a work in progress, with the complexity of integrating new systems and…