Author: Cybernoz
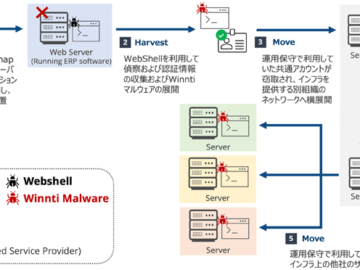
China-linked APT group Winnti targets Japanese organizations since March 2024 Pierluigi Paganini February 18, 2025 China-linked threat actor Winnti targeted…
Over the past 8 months, Luke (hakluke) Stephens and I have spoken with 10 security executives, surveyed over 550 security professionals,…
SectopRAT, also known as Arechclient2, is a sophisticated Remote Access Trojan (RAT) developed using the .NET framework. This malware is…
The New Snake Keylogger variant targets Windows users via phishing emails, using AutoIt for stealth. Learn how it steals credentials…
BlackLock is on track to become the most active ransomware-as-a-service (RaaS) outfit in 2025, according to ReliaQuest. Its success is…
By Autumn Stambaugh, Senior Sales Engineer at Pentera Think you’re safe because you’re compliant? Think again. Recent studies continue to…
A sophisticated malware campaign leveraging the Lumma InfoStealer has been identified, targeting educational institutions to distribute malicious files disguised as…
In recent years, cyber crime has evolved into a highly sophisticated and organized business model. One of the most alarming…
Feb 18, 2025Ravie LakshmananCyber Espionage / Malware The Chinese state-sponsored threat actor known as Mustang Panda has been observed employing…
Many companies from a range of industries worldwide are stuck at a trial stage of emerging technologies usage, according to…
Microsoft warns Apple developers about a new XCSSET malware variant targeting macOS, posing security risks through stealthy infections and data…
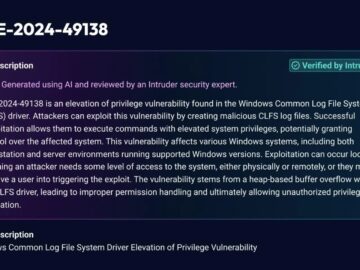
Intel by Intruder now uses AI to contextualize NVD descriptions, helping security teams assess risk faster. Intruder, a leader in…