Author: Cybernoz
ProcessUnity announced the next generation of the Global Risk Exchange. This platform transforms the third-party assessment process, reducing friction for…
Feb 18, 2025Ravie LakshmananVulnerability / Network Security Juniper Networks has released security updates to address a critical security flaw impacting…
Thank you for joining! Access your Pro+ Content below. 18 February 2025 AI Action Summit calls for a rethink of…
Feb 18, 2025The Hacker NewsArtificial Intelligence / Cyber Defense Is AI really reshaping the cyber threat landscape, or is the…
Meta has announced its plan for a subsea cable that will span the globe, connecting emerging economies such as India,…
Researchers from Trend Micro’s Threat Hunting team have uncovered a sophisticated cyberattack campaign by the advanced persistent threat (APT) group…
London-based managed service provider (MSP) Autodata Products has opted for Scality Artesca object storage through its Scality cloud service provider…
A cybersecurity incident at Zacks Investment Research has exposed sensitive data belonging to 12 million users, marking the second major…
Two critical vulnerabilities in LibreOffice (CVE-2024-12425 and CVE-2024-12426) expose millions of users to file system manipulation and sensitive data extraction…
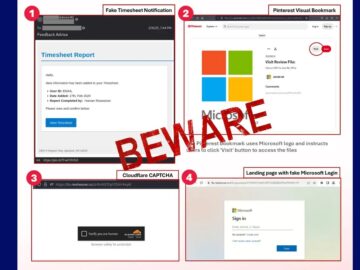
Cybersecurity researchers have uncovered a novel phishing campaign distributing the notorious Tycoon 2FA phishing kit through fraudulent timesheet notification emails,…
Xerox VersaLink C7025 Multifunction printer flaws may expose Windows Active Directory credentials to attackers Pierluigi Paganini February 18, 2025 Xerox…
The Directorate of Enforcement (ED) in Ahmedabad has dealt a significant blow to one of history’s largest cryptocurrency frauds, recovering Rs….