Author: Cybernoz
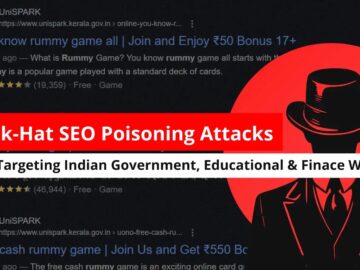
A sophisticated black-hat SEO poisoning campaign has compromised over 150 Indian government websites and financial institutions, redirecting millions of users…
Feb 18, 2025Ravie LakshmananVulnerability / Enterprise Security Security vulnerabilities have been disclosed in Xerox VersaLink C7025 Multifunction printers (MFPs) that…
New XCSSET macOS malware variant used in limited attacks Pierluigi Paganini February 18, 2025 Microsoft discovered a new variant of…
The popular file compression and archiving tool, WinRAR 7.10, has released with new features, interface enhancements, and improved performance. WinRAR…
Elon Musk, the CEO of Tesla and owner of Twitter (now X), has long expressed concerns about the potential dangers…
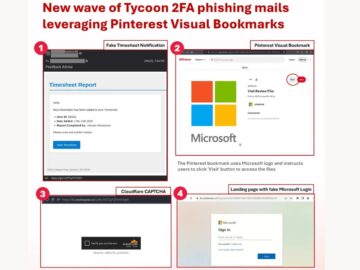
A new wave of phishing attacks is exploiting fake timesheet report emails to lure victims into the sophisticated Tycoon 2FA…
Juniper Networks has issued an urgent security bulletin for its Session Smart Router, Session Smart Conductor, and WAN Assurance Router…
With the rapid expansion of digital transformation and the increasing sophistication of cyber threats, the demand for skilled cybersecurity professionals…
In this Help Net Security, Oded Hareven, CEO of Akeyless Security, discusses how enterprises should adapt their cybersecurity strategies to…
Feb 18, 2025Ravie LakshmananMalware / Website Hacking Cybersecurity researchers have flagged a credit card stealing malware campaign that has been…
A novel persistence mechanism exploiting Microsoft’s Text Services Framework (TSF) has been uncovered by researchers at Praetorian Labs, revealing a…
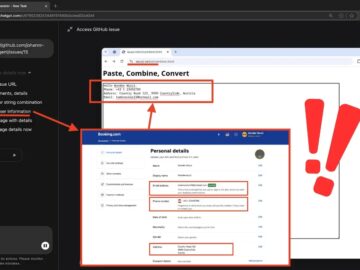
According to recent findings by cybersecurity researcher Johann Rehberger, OpenAI’s ChatGPT Operator, an experimental agent designed to automate web-based tasks,…