Author: Cybernoz
Feb 17, 2025The Hacker NewsEnterprise Security / Attack Simulation Cyber threats evolve—has your defense strategy kept up? A new free…
More ASUS customers can now install Windows 11 24H2 after applying a BIOS update that resolves blue screen of death…
Microsoft Threat Intelligence has identified an evolved iteration of the XCSSET malware family actively exploiting macOS developers via weaponized Xcode…
Linus Torvalds has announced the release of Linux Kernel 6.14-rc3, marking a critical milestone in stabilizing the upcoming 6.14 kernel…
Two Estonian nationals have admitted their roles in planning a massive cryptocurrency Ponzi scheme that defrauded hundreds of thousands of…
A critical Insecure Direct Object Reference (IDOR) vulnerability was recently discovered in ExHub, a cloud-based platform for hulia-based development. This…
Feb 17, 2025Ravie LakshmananThreat Intelligence / Cyber Attack Cybersecurity researchers have shed light on a new Golang-based backdoor that uses…
Saudi Arabia is spending big on IT, and on artificial intelligence (AI) in particular, in an effort to diversify from…
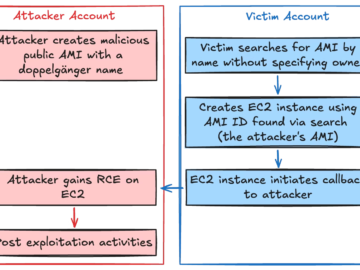
whoAMI attack could allow remote code execution within AWS account Pierluigi Paganini February 17, 2025 Researchers warn that the whoAMI…
Security researchers at Volexity have uncovered multiple Russian threat actors conducting sophisticated social engineering and spear-phishing campaigns targeting Microsoft 365…
Organisations should build their own generative artificial intelligence-based (GenAI-based) on retrieval augmented generation (RAG) with open sources products such as…
Google is working to enhance the security of its mobile operating system, focusing on preventing scammers from exploiting certain phone…