Author: Cybernoz
Google has rolled out a new security update for Chrome users, following the discovery of a vulnerability, CVE-2025-2783, affecting the…
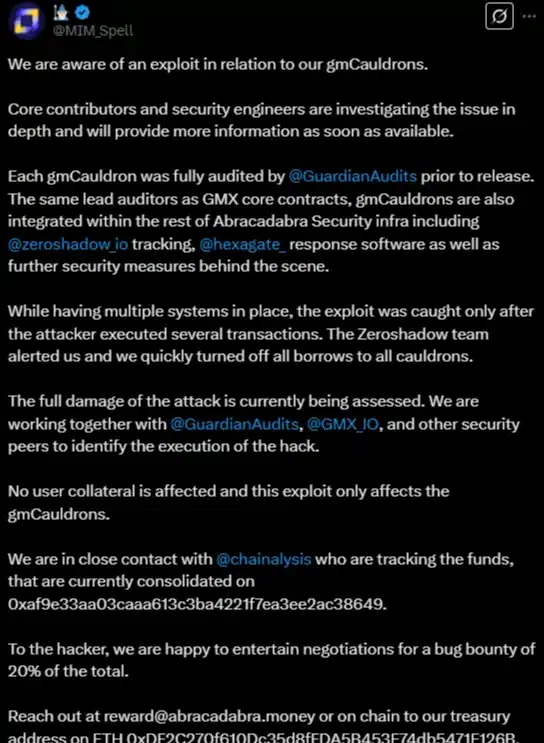
The decentralized finance (DeFi), Abracadabra, is dealing with a cyberattack that resulted in the theft of nearly $13 million worth…
NSW Department of Customer Service (DCS) has tapped Naomi Youness to temporarily lead IT as CIO Aarti Joshi embarks on…
I have a confession to make: I’m using a Chrome-based browser again. This time, I’m trying out Microsoft Edge. The…
BlackLock Ransomware Targeted by Cybersecurity Firm Pierluigi Paganini March 26, 2025 Resecurity found an LFI flaw in the leak site…
SECURITY | AI | PURPOSEUNSUPERVISED LEARNING is a newsletter about upgrading to thrive in a world full of AI. It’s…
2025년 시작과 함께 ZAP 2.16이 릴리즈되었습니다 이번 업데이트는 기능적으로 추가된 부분들이 있어서 대표적인 기능 3가지 위주로 정리하면서 리뷰할까 합니다. Client…
Amelia Coen | 10 January 2025 at 15:53 UTC Extensibility in Burp Suite is about giving you and your team…
AI-powered web vuln scanner agent and Baby Naptime, 2 tools + guides on preventing ransomware in AWS, detailed guide on…
Dive Brief: Wiz researchers on Monday disclosed the technical details of four critical vulnerabilities — CVE-2025-1097, CVE-2025-1098, CVE-2025-24514 and CVE-2025-1974…
President Donald Trump issued an executive order Tuesday that threatens states with the loss of federal election grants unless they…
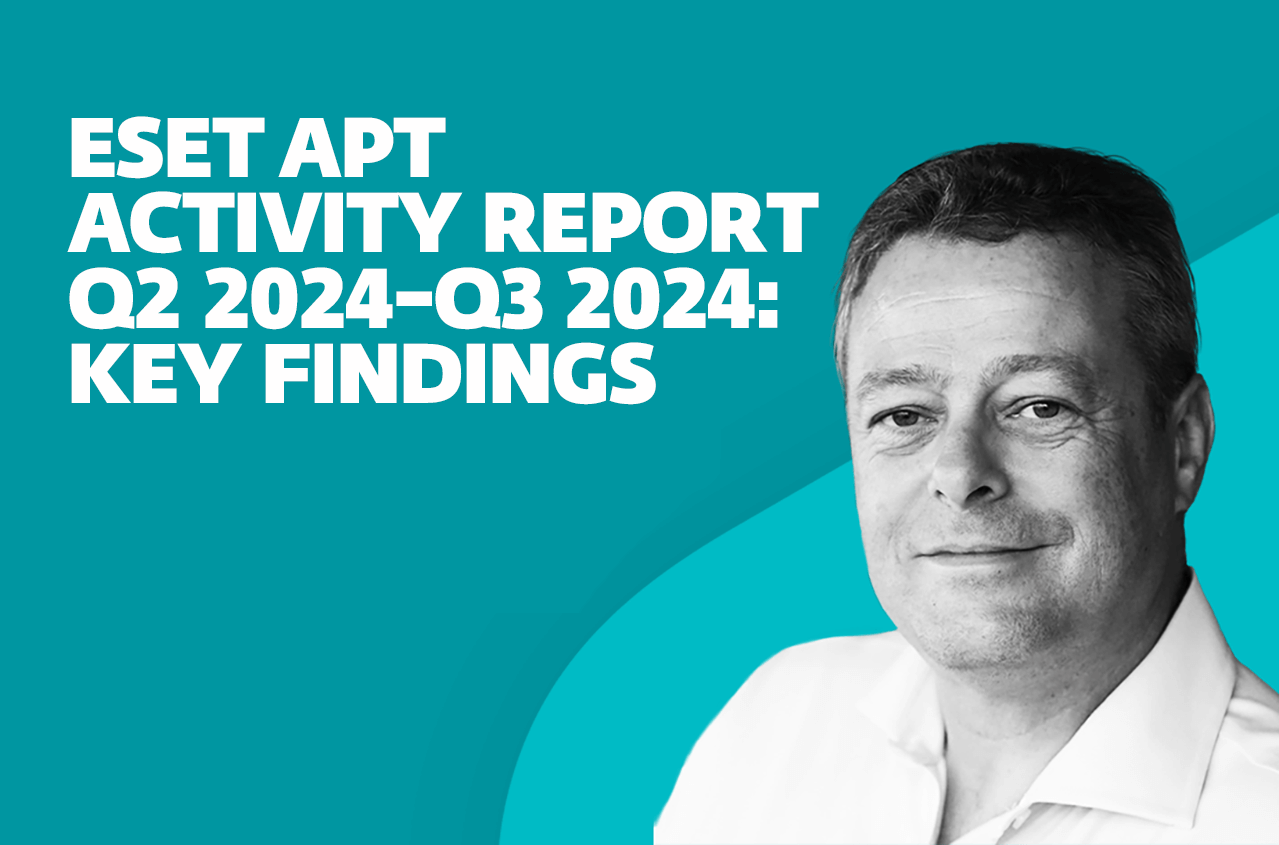
ESET Chief Security Evangelist Tony Anscombe highlights some of the most intriguing insights revealed in the latest ESET APT Activity…







![[tl;dr sec] #269 – New AI Security Tools, Ransomware in AWS, How to Hack AI Apps [tl;dr sec] #269 - New AI Security Tools, Ransomware in AWS, How to Hack AI Apps](https://image.cybernoz.com/wp-content/uploads/2025/03/1743077918_tldr-sec-269-New-AI-Security-Tools-Ransomware-in.png)