Author: Cybernoz
In partnership with The internet is wild right now. Yesterday’s meme coin is today’s fortune. Social media musical chairs. Here’s…
Android malware campaigns use .NET MAUI to evade detection Pierluigi Paganini March 25, 2025 Researchers warn of a new Android…
The three settings I had to enable to get proper WiFi roaming The problem I’m a massive fan of Ubiquiti…
How Google eliminates vuln classes, human expert-level AI spear phishing, how Palantir hardens their code writing process I hope you’ve…
A Canadian citizen is one step closer to standing trial in the United States for his alleged involvement in a…
The trailblazing scientist shares her reasons for hope in the fight against climate change and how we can tackle seemingly…
You can’t escape AI in WhatsApp even if you are based in one of the 41 European countries. Today, more…
Organizations are facing an unbelievable surge in cloud-based security threats, with attacks nearly five times more frequent at the end…
Selecting the right Laptop For Cybersecurity is one of the most critical decisions for cybersecurity professionals. Whether you are a CISO, penetration…
INE, a global leader in networking and cybersecurity training and certifications, is proud to announce it is the recipient of…
The Humanized Internet: Dignity, Digital Identity and Democracyhttps://www.riverpublishers.com/book_details.php?book_id=671 What does it mean to have a humanized Internet? How can we…
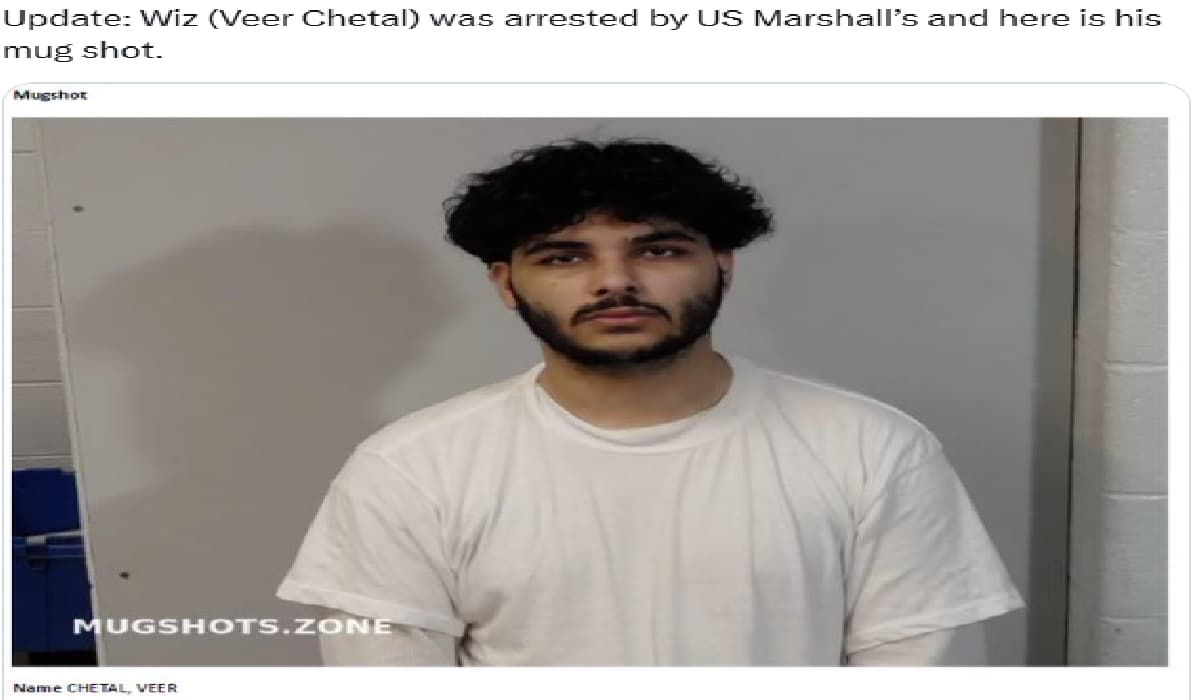
In a new development in the investigation of a massive $243 million cryptocurrency heist, one of the key suspects, Veer…

![[tl;dr sec] #265 – Google’s Secure-by-Design Web Framework, AI-powered Phishing, How Palantir Secures Source Control [tl;dr sec] #265 - Google's Secure-by-Design Web Framework, AI-powered Phishing, How Palantir Secures Source Control](https://image.cybernoz.com/wp-content/uploads/2025/03/tldr-sec-265-Googles-Secure-by-Design-Web-Framework-AI-powered-Phishing.png)