Author: Cybernoz
Oxford Semantic Technologies, is an example of what Matt Clifford, chair of the Advanced Research and Invention Agency (ARIA), was…
UTA’s Wang notes that while she hasn’t assessed whether scammers are using generative AI to produce romance scam scripts, she…
In most cases, thieves disappear after successfully stealing money, goods, or valuable data. However, in the world of cybercrime, particularly…
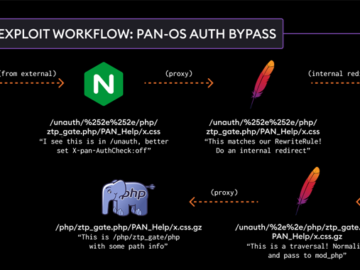
Feb 13, 2025Ravie LakshmananNetwork Security / Vulnerability Palo Alto Networks has addressed a high-severity security flaw in its PAN-OS software…
The UK government has sanctioned Russian entity Zservers, as well as six individual members of the cyber group and its…
Feb 13, 2025Ravie LakshmananMalware / Cyber Espionage Threat hunters have shed light on a new campaign targeting the foreign ministry…
Salvador Tech introduced a Edge-Recovery Platform, a leap forward in comprehensive cyber resilience in the Operational Technology (OT) and Industrial…
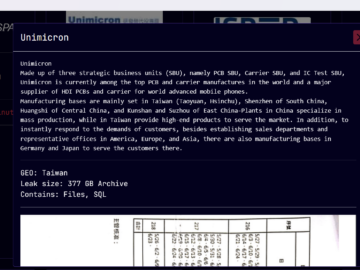
Sarcoma ransomware gang claims the theft of sensitive data from PCB maker Unimicron Pierluigi Paganini February 13, 2025 The Sarcoma…
In the world of cybersecurity, Third-Party Risk Management has fundamentally focused on measurable risks such as data breaches, intellectual property…
The United Kingdom government has secretly requested that Apple build a backdoor into its iCloud service, granting the government unrestricted…
When the Chinese hacker group known as Salt Typhoon was revealed last fall to have deeply penetrated major US telecommunications…
More than three million employee-linked corporate accounts were compromised between 2022 and 2024 across Fortune 500 companies, according to Enzoic….