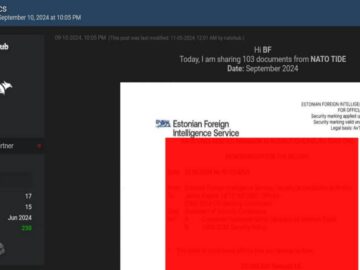
Author: Cybernoz
PlayStation Network Down: PSN is experiencing a major outage, affecting account login, online gaming, PlayStation Store, and more. No fixed…
Talent Isn’t Your Savior, It’s Your Ceiling Talent is a high-risk gift. On the positive side, it gives you a…
PlayStation Network outage has been going on for over 24 hours Pierluigi Paganini February 08, 2025 PlayStation Network has been…
LLMjacking attacks target DeepSeek, racking up huge cloud costs. Sysdig reveals a black market for LLM access has emerged, with…
Kimsuky APT group used custom RDP Wrapper version and forceCopy stealer Pierluigi Paganini February 08, 2025 Researchers spotted North Korea’s…
A large-scale brute force password attack using almost 2.8 million IP addresses is underway, attempting to guess the credentials for…
It can be difficult to fully appreciate just what has changed when it comes to cybersecurity – and by how…
Russia’s intelligence recruits Ukrainians for terror attacks via messaging apps Pierluigi Paganini February 08, 2025 Russia’s intelligence recruits Ukrainians for…
Today’s business environment requires teams to do more — better than before, and at a faster rate. Thanks to third-party…
NAKIVO is one of the first data backup solution providers to support data protection for Proxmox virtual environments SPARKS, Nevada…
A joint operation between the National Police and the Civil Guard concluded in the arrest of a suspected cybercriminal in…
As Elon Musk and his so-called Department of Government Efficiency rampage through United States federal institutions, WIRED reported extensively this…