Author: Cybernoz
US-based construction, geospatial and transportation technology solutions provider Trimble has warned customers of its Cityworks product about a vulnerability that…
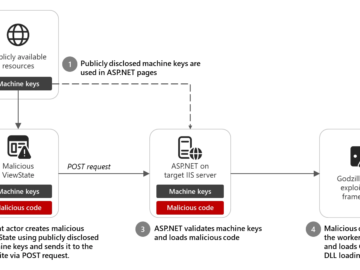
Attackers used a public ASP.NET machine to conduct ViewState code injection attacks Pierluigi Paganini February 07, 2025 Microsoft researchers warn…
The way we manage digital identity is fundamentally broken. The root of the problem lies in traditional, centralized identity models,…
A recent security incident has revealed that over 3,000 publicly disclosed ASP.NET machine keys were exploited by hackers to execute…
Splunk, a leader in data analytics and cybersecurity solutions, has introduced a groundbreaking proof-of-concept honeypot system named DECEIVE (DECeption with…
UK uses Richter Scale measurement for Cyber Attacks The United Kingdom has introduced a groundbreaking new method for assessing the…
As I write this, the front page of GitHub.com declares in big bold letters that this is “Where the world…
NSA’s Research Directorate released version 11.3 of Ghidra, an open-source software reverse engineering (SRE) framework. It offers advanced analysis tools,…
Feb 07, 2025Ravie LakshmananVulnerability / Threat Intelligence Threat actors have been observed exploiting recently disclosed security flaws in SimpleHelp’s Remote…
The implementation of new regulatory measures that impact the UK, EU, and beyond are driving organizations to enhance vigilance in…
Times and technologies change, but a few good ideas are still the same. With consistent application, a handful of wise…
Cyber fraud (which includes activity such as hacking, deepfakes, voice cloning and highly sophisticated phishing schemes) rose by 14% year…