Author: Cybernoz
Austin, TX, USA, February 4th, 2025, CyberNewsWire SpyCloud’s Identity Threat Protection solutions spearhead a holistic identity approach to security, illuminating…
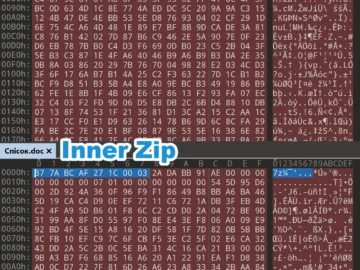
CVE-2025-0411, a Mark-of-the-Web bypass vulnerability in the open-source archiver tool 7-Zip that was fixed in November 2024, has been exploited…
Feb 04, 2025Ravie LakshmananVulnerability / Cyber Espionage A recently patched security vulnerability in the 7-Zip archiver tool was exploited in…
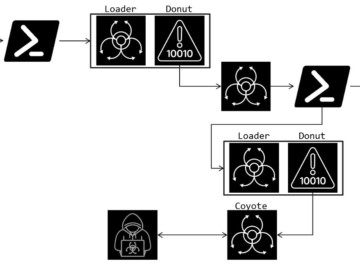
Coyote Banking Trojan targets Brazilian users, stealing data from 70+ financial apps and websites Pierluigi Paganini February 04, 2025 Coyote…
A new security vulnerability, identified as CVE-2025-24860, has been disclosed in Apache Cassandra, a widely used distributed database system. The…
SmartApeSG, a FakeUpdate cyber threat, has emerged as a significant vector for delivering NetSupport RAT, a maliciously exploited remote administration…
N. Korean ‘FlexibleFerret’ malware targets macOS with fake Zoom apps, job scams, and bug report comments, deceiving users into installation….
Nymi launched next-generation wearable authenticator, the Nymi Band 4, which introduces design upgrades and expanded passwordless use cases for regulated…
Researchers from the Positive Technologies Expert Security Center (PT ESC) have identified and prevented a malicious campaign targeting users of…
Apple, one of the most trusted technology brands in the world, recently faced a critical security exposure in its service…
Feb 04, 2025The Hacker NewsThreat Detection / Cloud Security As cloud security evolves in 2025 and beyond, organizations must adapt…
Despite rising demand for data-driven insights, a high share of mission-critical IT is either approaching or already at end of…