Author: Cybernoz
Amazon Web Services (AWS) has announced significant updates to its popular data warehousing service, Amazon Redshift, with the introduction of…
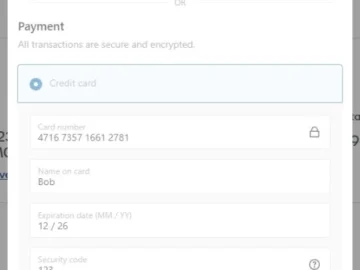
Japanese electronics maker Casio has had its UK website injected with a web skimmer that collected buyers’ personal and payment…
Thank you for joining! Access your Pro+ Content below. 4 February 2025 The need for strong data engineering skills Share…
A new variant of malware, known as FlexibleFerret, has been identified targeting macOS users while evading detection by Apple’s XProtect…
In a significant finding, Forcepoint’s X-Labs research team has uncovered a new malware campaign that uses AsyncRAT, a notorious remote…
Feb 04, 2025Ravie LakshmananVulnerability / Hardware Security A security vulnerability has been disclosed in AMD’s Secure Encrypted Virtualization (SEV) that…
Hackers have exploited a zero-day vulnerability in the popular file archiver 7-Zip to deploy SmokeLoader malware. The vulnerability, tracked as…
In a significant advancement in AI safety, the Anthropic Safeguards Research Team has introduced a cutting-edge framework called Constitutional Classifiers…
Taiwan has become the latest country to ban government agencies from using Chinese startup DeepSeek’s Artificial Intelligence (AI) platform, citing…
Food delivery company GrubHub disclosed a data breach impacting the personal information of an undisclosed number of customers, merchants, and…
U.S. prosecutors have charged Andean Medjedovic, a 22-year-old Canadian, with five counts of criminal indictment for allegedly orchestrating a sophisticated…
Schools have faced an onslaught of cyberattacks since the pandemic disrupted education nationwide five years ago, yet district leaders across…