Author: Cybernoz
While organizations have long experimented with various facets of digital transformation, the journey toward crypto-agility is one of the most…
In this Help Net Security interview, Benjamin Racenberg, Senior Intelligence Services Manager at Nisos, discusses the threat of workforce fraud,…
GenAI offers financial services institutions enormous opportunities, particularly in unstructured dataset analysis and management, but may also increase security risks,…
Feb 04, 2025Ravie LakshmananVulnerability / SharePoint Cybersecurity researchers have disclosed details of a now-patched vulnerability impacting the Microsoft SharePoint connector…
Google fixed actively exploited kernel zero-day flaw Pierluigi Paganini February 04, 2025 The February 2025 Android security updates addressed 48…
The first Apple-notarized porn app, “Hot Tub,” is now available to iPhone users in Europe through the alternative app marketplace,…
Cybersecurity researchers at the Positive Technologies Expert Security Center (PT ESC) have found a sneaky malware campaign targeting the Python Package…
Nationwide Building Society said it wants to add cyber security training to its programme, which has fast-tracked more than 300…
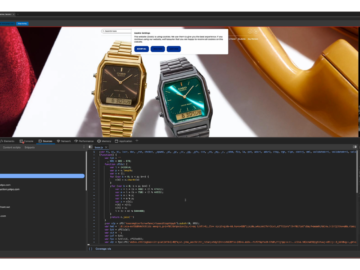
Web Skimmer found on at least 17 websites, including Casio UK Pierluigi Paganini February 03, 2025 A threat actor has…
The healthcare industry has become increasingly reliant on technology to enhance patient care, from advanced image-guided surgery to computerized provider…
Amazon has announced key security enhancements for Redshift, a popular data warehousing solution, to help prevent data exposures due to…
Australia’s government carved out an exemption for YouTube when it passed laws banning social media access for children under 16,…