Author: Cybernoz
A new threat to cybersecurity has emerged in the form of Devil-Traff, a bulk SMS platform designed to facilitate large-scale…
As organizations increasingly adopt Infrastructure as Code (IaC) to automate and manage their cloud environments, ensuring the security of these…
Authorities have successfully disrupted and dismantled the notorious online cybercrime marketplaces known as Cracked and Nulled, which had been operating…
Law enforcement seized the domains of HeartSender cybercrime marketplaces Pierluigi Paganini February 03, 2025 U.S. and Dutch authorities seized 39…
As the digital world continues to evolve, so does the threat landscape, with cyberattacks growing more sophisticated and frequent. In…
Google Warns Users About AI-Driven Phishing Scam Google has issued an urgent warning to its 2.5 billion active users about…
In this Help Net Security interview, Rob Lee, Chief of Research and Head of Faculty at SANS Institute, discusses what…
A Russian-speaking cybercrime gang known as Crazy Evil has been linked to over 10 active social media scams that leverage…
BadDNS is an open-source Python DNS auditing tool designed to detect domain and subdomain takeovers of all types. BadDNS modules…
The Australian Securities and Investments Commission (ASIC) has opened an investigation into a technical issue with the Australian Securities Exchange…
Mid-market organizations are grappling with managing the large volume of SaaS applications, both sanctioned and unsanctioned, with actual numbers often…
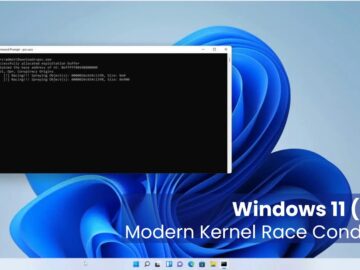
A sophisticated race condition vulnerability affecting Windows 11 (x64) kernel operations, highlighting ongoing concerns about kernel-level security in modern operating…