Author: Cybernoz
The IoT Security Foundation’s fifth annual report into the state of vulnerability disclosure consumer Internet of Things, produced by Copper…
Cybercriminals recently exploited Google’s g.co subdomain to carry out a meticulously crafted scam over a vishing call. The incident was…
Hackers Report The Most Vulnerabilities In 2022 To Keep The Platform Secure We looked at how our program performed from…
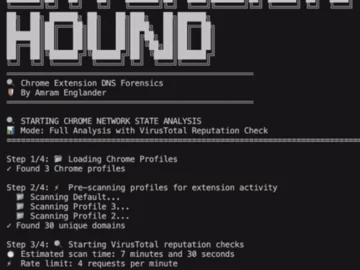
Traditional monitoring tools reveal only traffic from the Chrome process, leaving security teams uncertain about which extension is responsible for…
Cybercriminals are increasingly exploiting vulnerabilities in government websites to carry out phishing campaigns, leveraging the inherent trust users place in…
DeepSeek AI, a Chinese chatbot service that recently gained traction on the Apple App Store, is now in the spotlight…
In this Help Net Security interview, Sean Cordero, CISO at Zscaler, talks about securing hybrid work and the new challenges…
Use Code Security Audit for DevOps DevOps teams may care about security, but it is not their area of expertise…
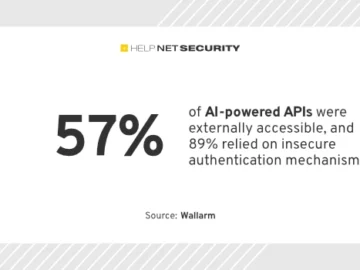
APIs have emerged as the predominant attack surface over the past year, with AI being the biggest driver of API…
Hide My Email is a service that comes with iCloud+, Apple’s subscription-based service. It allows users to generate one-time-use or…
1. Discover and Import Maintaining an up-to-date inventory of all your internet-facing assets is crucial for effective risk…
The allure of generative AI and the importance of the basics. While the advent of generative AI poses new challenges,…