Author: Cybernoz
Whitehall, a term that refers both to the British government administration and a specific geographic location in central London, has…
Jan 29, 2025Ravie LakshmananVulnerability / Network Security Cybersecurity researchers are warning that a critical zero-day vulnerability impacting Zyxel CPE Series…
Attackers exploit SimpleHelp RMM Software flaws for initial access Pierluigi Paganini January 29, 2025 Threat actors exploit recently fixed SimpleHelp…
Earlier this year, I was part of a HackerOne team that developed the Women in Sales Employee Resource Group (ERG)….
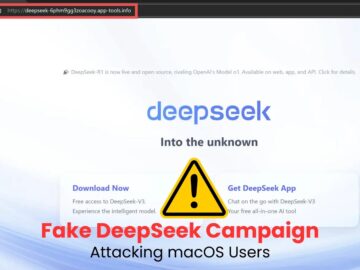
A new cyberattack campaign, dubbed the “Fake DeepSeek Campaign,” has been discovered targeting macOS users. DeepSeek, a Chinese-developed AI chatbot, has…
A recent security vulnerability in a widely used airline integration service has exposed millions of users to account takeovers, raising…
As organizations continue to migrate to the cloud to enhance scalability, flexibility, and cost efficiency, the role of data engineers…
The Australian government has announced a $6.4 million grant to the Critical Infrastructure – Information Sharing and Analysis Centre (CI-ISAC)…
Jan 29, 2025Ravie LakshmananVulnerability / Software Security Broadcom has alerted of a high-severity security flaw in VMware Avi Load Balancer…
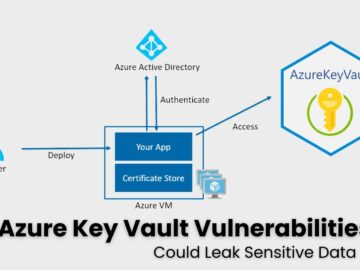
A detailed walkthrough demonstrates how attackers can manipulate Azure Key Vault’s access policies after compromising Entra ID (formerly Azure AD)…
A recently discovered Cross-site Scripting (XSS) vulnerability, CVE-2024-57514, affecting the TP-Link Archer A20 v3 Router has raised security concerns among…
In this Help Net Security interview, James Mirfin, SVP and Head of Risk and Identity Solutions at Visa, discusses key…