Author: Cybernoz
Jan 29, 2025Ravie LakshmananCyber Espionage / Threat Intelligence The advanced persistent threat (APT) group known as UAC-0063 has been observed…
The rapid adoption of artificial intelligence (AI) has triggered both excitement and unease in the cybersecurity community. On one hand,…
The rapid adoption of artificial intelligence (AI) has triggered both excitement and unease in the cybersecurity community. On one hand,…
The HackerOnesie instantly became famous the day it was introduced in 2017. Although it has been known to carry magical…
Cloudflare revealed how its data pipeline has achieved unprecedented scalability, processing up to 706 million events per second as of…
The number of US data compromises in 2024 (3,158) decreased 1% compared to 2023 (3,202), 44 events away from tying…
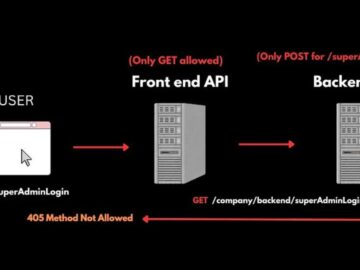
Cybersecurity researchers have exposed critical vulnerabilities in a telecom network that allowed unauthorized access to sensitive data and control over…
Ransomware attacks are disrupting and undermining business operations and draining revenue streams, according to Illumio. Findings from the study reveal…
The program began in 2021 as an internal resource for engineers to be mentors and mentees. Mentors build their leadership…
A financially motivated threat actor has been linked to a sophisticated cyber campaign that has been targeting users in Poland…
PowerSchool, a leading U.S.-based education technology provider, has begun notifying students, teachers, and other affected individuals following a massive data…
The rule requires public companies to report material cybersecurity incidents and annually report on elements of their cybersecurity risk management…