Author: Cybernoz
Given digital technology is so central to how we live, work, transact and communicate, we have recently seen the finalisation…
Generative AI (GenAI) has quickly become a core in enterprise environments, but with its growing adoption comes significant security concerns….
Union County, Pennsylvania, has fallen victim to a ransomware attack that compromised personal information belonging to its more than 40,000…
Microsoft has abandoned data centre projects set to use two (2) gigawatts of electricity in the US and Europe in…
A while ago I asked what you wanted me to improve. This led to me revamping part of my premium…
Google fixed the first actively exploited Chrome zero-day since the start of the year Pierluigi Paganini March 26, 2025 Google…
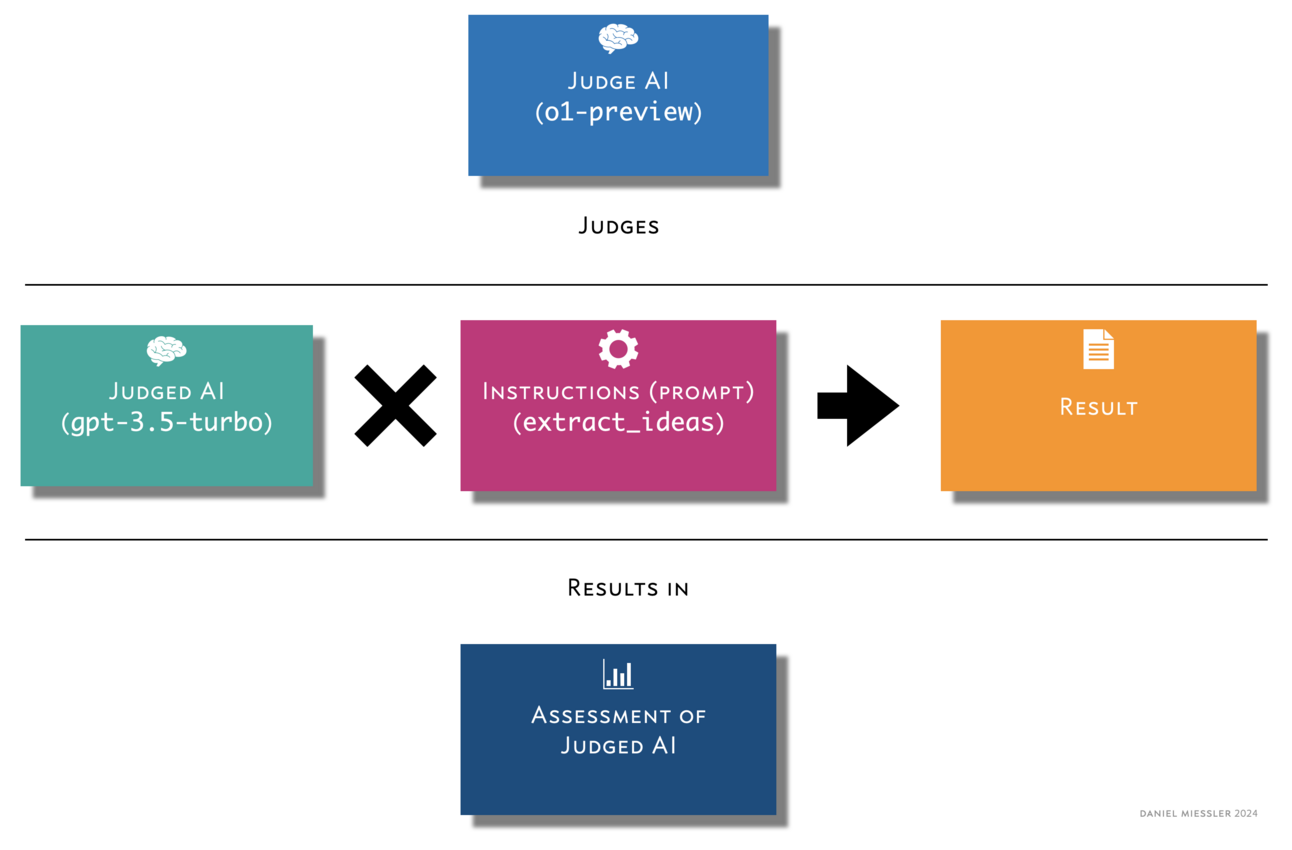
The structure of the rate_ai_result Stitch Since early 2023 I’ve wanted a system that can assess how well AI does…
Nov 03, 2024 Detecting Secrets with Noir – The PassiveScan Advantage Hello, security enthusiasts! Today, we’re diving into the exciting…
Amelia Coen | 12 September 2024 at 11:55 UTC Hands-on security testers need the best tools for the job. Tools…
How Burp Suite is adding AI-powered features, understanding and mitigating OAuth vulns, a PoC to subtly backdoor an LLM I…
Dive Brief: Security researchers said they confirmed a breach of Oracle Cloud after a previously unknown threat actor posted an…
Democratic senators hammered two top national security officials Tuesday about their participation in a Signal chat discussing war plans that reportedly…







![[tl;dr sec] #268 – AI-powered Burp Suite, OAuth Vulnerabilities, Subtle LLM Backdoors [tl;dr sec] #268 - AI-powered Burp Suite, OAuth Vulnerabilities, Subtle LLM Backdoors](https://image.cybernoz.com/wp-content/uploads/2025/03/1743080265_tldr-sec-268-AI-powered-Burp-Suite-OAuth-Vulnerabilities-Subtle.png)

