Author: Cybernoz
Amazon Web Services (AWS) has reported a 19% year-on-year (YoY) increase in revenue for the second successive quarter in its…
The UK government has reportedly issued a secret order to Apple, compelling the tech giant to create a backdoor for…
A critical zero-day vulnerability has been discovered in Microsoft Sysinternals tools, posing a serious security threat to IT administrators and developers worldwide….
Small and medium businesses (SMBs) play a massive role in the economy and, in the UK private sector alone, account…
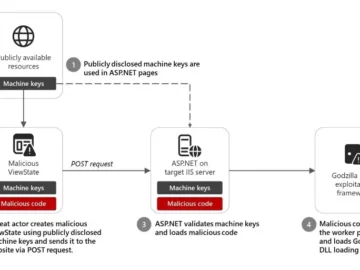
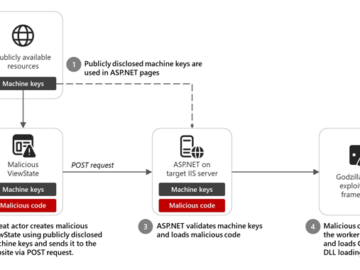
A ViewState code injection attack spotted by Microsoft threat researchers in December 2024 could be easily replicated by other attackers,…
Feb 07, 2025Ravie LakshmananCloud Security / Web Security Microsoft is warning of an insecure practice wherein software developers are incorporating…
Microsoft Edge 133 is now rolling out globally, and it ships with several improvements, including a new scareware blocker feature….
A new attack vector exploiting vulnerabilities in Kerberos delegation within Active Directory (AD) networks has been uncovered, posing significant risks…
A critical security vulnerability has been identified and disclosed in the Logsign Unified SecOps Platform, allowing remote attackers to bypass…
The foundations for social engineering attacks – manipulating humans – might not have changed much over the years. It’s the…
The personal and health information of over 430,000 individuals was compromised in October and November 2024 data breaches at Allegheny…
Windows 11’s January 28 optional update has fixed a long-standing issue in Windows 11 24H2 that prevents non-admin users from…