Author: Cybernoz
While malware attacks embedded in games have been a longstanding cybersecurity concern, a more sinister threat has emerged. Researchers have…
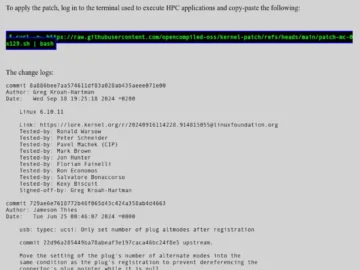
A threat actor tracked as MUT-1244 by DataDog researchers has been targeting academics, pentesters, red teamers, security researchers, as well…
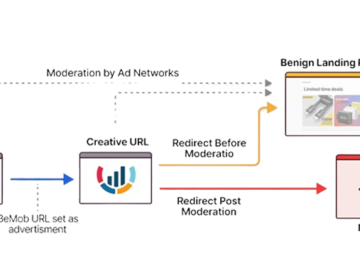
Dec 16, 2024Ravie LakshmananMalvertising / Threat Intelligence Cybersecurity researchers have shed light on a previously undocumented aspect associated with ClickFix-style…
It is no surprise that artificial intelligence (AI) is having a big impact on software development, given the hype across…
The Serbian government exploited Qualcomm zero-days to unlock and infect Android devices with a new spyware named ‘NoviSpy,’ used to spy…
It’s clear that a person’s reputation is increasingly influenced by their online presence, which spans platforms like LinkedIn, corporate websites,…
This year has been a year of political and economic turmoil around the world – and one where the top…
The research identified vulnerabilities in Prometheus, including information disclosure from exposed servers, DoS risks from pprof endpoints, and potential code…
Microsoft has announced that it is currently blocking an astounding 7,000 password attacks every second, nearly double the rate from…
16 Dec The clear and present danger of AI-powered attacks, and how to defeat them Posted at 08:49h in Blogs…
Computer Weekly Buyer’s Guides map the IT buying cycle of our readership onto relevant editorial that will inform and educate…
Recent cyberattacks targeting critical infrastructure, including fuel management systems and water treatment facilities in Israel and the US, have been…