Author: Cybernoz
Malware peddlers are using NodeLoader, a loader written in Node.js, to foil security solutions and deliver infostealers and cryptominers to…
Dec 16, 2024Ravie LakshmananSpyware / Surveillance A Serbian journalist had his phone first unlocked by a Cellebrite tool and subsequently…
Being the chief information security officer (CISO) for a major supplier brings challenges: you’re working with people who understand your…
Researchers identified a threat actor leveraging Google Search ads to target graphic design professionals, as the actor has launched at…
Brands are increasingly seen to be employing familiar and expensive faces to ambassador ad campaigns and new products. However, with…
Find out the key security risks of firmware security: Identify threats, and learn best practices and protection methods against modern…
Hackers have begun exploiting a newly discovered vulnerability in Apache Struts2, a widely used open-source framework for developing Java web…
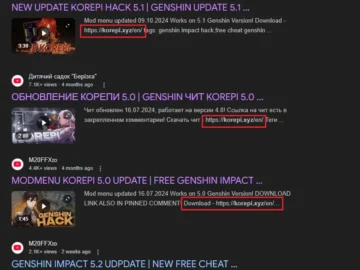
summary Phishing Attack: Cybercriminals use fake brand collaboration emails to target YouTube creators. Malware Disguise: Malicious files are hidden in…
As part of a pilot roll-out, the IT service department at the University of Oxford has run a week-long survey…
A second CISA employee predicts that “compliance efforts like secure-by-design may not have the support that they currently benefit from.”…
Recent cybersecurity research has uncovered a concerning trend where hackers are exploiting Microsoft Teams to gain remote access to victim…
With the evolution of modern software development, CI/CD pipeline governance has emerged as a critical factor in maintaining both agility…