Author: Cybernoz
16 Dec The clear and present danger of AI-powered attacks, and how to defeat them Posted at 08:49h in Blogs…
Computer Weekly Buyer’s Guides map the IT buying cycle of our readership onto relevant editorial that will inform and educate…
Recent cyberattacks targeting critical infrastructure, including fuel management systems and water treatment facilities in Israel and the US, have been…
Malware peddlers are using NodeLoader, a loader written in Node.js, to foil security solutions and deliver infostealers and cryptominers to…
Dec 16, 2024Ravie LakshmananSpyware / Surveillance A Serbian journalist had his phone first unlocked by a Cellebrite tool and subsequently…
Being the chief information security officer (CISO) for a major supplier brings challenges: you’re working with people who understand your…
Researchers identified a threat actor leveraging Google Search ads to target graphic design professionals, as the actor has launched at…
Brands are increasingly seen to be employing familiar and expensive faces to ambassador ad campaigns and new products. However, with…
Find out the key security risks of firmware security: Identify threats, and learn best practices and protection methods against modern…
Hackers have begun exploiting a newly discovered vulnerability in Apache Struts2, a widely used open-source framework for developing Java web…
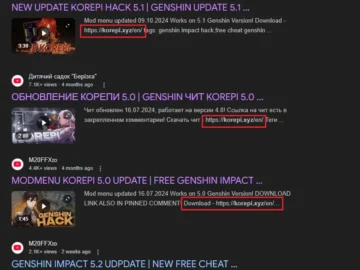
summary Phishing Attack: Cybercriminals use fake brand collaboration emails to target YouTube creators. Malware Disguise: Malicious files are hidden in…
As part of a pilot roll-out, the IT service department at the University of Oxford has run a week-long survey…