Author: Cybernoz
Hackers have begun exploiting a newly discovered vulnerability in Apache Struts2, a widely used open-source framework for developing Java web…
summary Phishing Attack: Cybercriminals use fake brand collaboration emails to target YouTube creators. Malware Disguise: Malicious files are hidden in…
As part of a pilot roll-out, the IT service department at the University of Oxford has run a week-long survey…
A second CISA employee predicts that “compliance efforts like secure-by-design may not have the support that they currently benefit from.”…
Recent cybersecurity research has uncovered a concerning trend where hackers are exploiting Microsoft Teams to gain remote access to victim…
With the evolution of modern software development, CI/CD pipeline governance has emerged as a critical factor in maintaining both agility…
Hackers leveraged Microsoft Teams to manipulate a victim into granting remote access to their system. The attack, analyzed by Trend…
Digital license plates, already legal to buy in a growing number of states and to drive with nationwide, offer a…
Cybersecurity researchers have discovered a new PHP-based backdoor called Glutton that has been put to use in cyber attacks targeting…
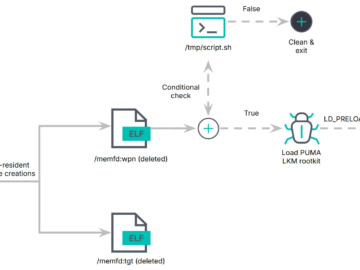
PUMAKIT, a sophisticated rootkit that uses advanced stealth mechanisms Pierluigi Paganini December 15, 2024 Researchers discovered PUMAKIT, a Linux rootkit…
A new wave of cyberattacks has emerged, targeting YouTube creators through malicious collaboration requests that exploit the trust between creators…
Dec 16, 2024Ravie LakshmananCryptocurrency / Phishing Attack Cybersecurity researchers are calling attention to a new kind of investment scam that…