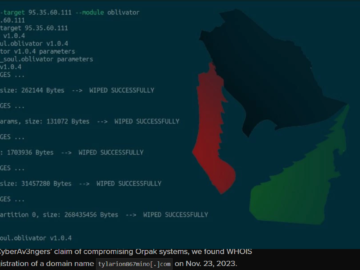
Author: Cybernoz
A critical security flaw has been discovered in the popular data transfer tool Curl, potentially allowing attackers to access sensitive…
The original version of this story appeared in Quanta Magazine. For thousands of years, if you wanted to send a…
The holiday season is largely characterized by a significant rise in consumer spending, and digital deals for Black Friday and…
IOCONTROL cyberweapon used to target infrastructure in the US and Isreael Pierluigi Paganini December 14, 2024 Iran-linked threat actors target…
Russian cyberspies Gamaredon has been discovered using two Android spyware families named ‘BoneSpy’ and ‘PlainGnome’ to spy on and steal…
A threat actor tracked as MUT-1244 has stolen over 390,000 WordPress credentials in a large-scale, year-long campaign targeting other threat…
U.S. CISA adds Cleo Harmony, VLTrader, and LexiCom flaw to its Known Exploited Vulnerabilities catalog Pierluigi Paganini December 14, 2024 U.S….
File upload vulnerabilities are fun to find, they are impactful by nature and in some cases even result in remote…
Maintaining a resilient, secure, and efficient network infrastructure is more important than ever. Network monitoring systems, which encompass both hardware…
Dec 14, 2024Ravie LakshmananBotnet / Ad Fraud Germany’s Federal Office of Information Security (BSI) has announced that it has disrupted…
In a significant turn towards a passwordless future, Microsoft has announced groundbreaking strides in adopting passkeys, a secure and user-friendly…
What a week! On Monday, police arrested 26-year-old Luigi Mangione and charged him in the murder of UnitedHealthcare CEO Brian…