Author: Cybernoz
SUMMARY Sanctions on Chinese Firm: The US sanctioned Sichuan Silence Information Technology and employee Guan Tianfeng for exploiting a firewall…
SUMMARY Global Dismantling of DDoS Platforms: Law enforcement from 15 countries shut down 27 websites offering DDoS attack services as…
Network security is now an important part of keeping a company safe in this digital age where cyber threats are…
Google’s first step into the cloud was App Engine, launched in 2008. Google Cloud Storage followed later in 2010. Since…
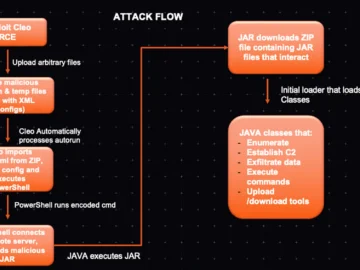
Cleo has released security updates for a zero-day flaw in its LexiCom, VLTransfer, and Harmony software, currently exploited in data…
tomertu – stock.adobe.com By Published: 12 Dec 2024 Artificial intelligence (AI) is no longer just a buzzword; it’s a transformative…
The Spanish police, working with colleagues in Peru, conducted a simultaneous crackdown on a large-scale voice phishing (vishing) scam ring…
Byte Federal, one of the largest Bitcoin ATM operators in the United States, has reported a significant data breach affecting…
Cleo has released a security patch to address the critical vulnerability that started getting exploited while still a zero-day to…
Senators introduced a bill on Tuesday that would prohibit data brokers from selling or transferring location and health data. Data…
Change appears to be afoot in the threat landscape, according to NCC Group’s latest monthly Threat pulse report for November,…
US Bitcoin ATM operator Byte Federal has disclosed a data breach that exposed the data of 58,000 customers after its…