Author: Cybernoz
For years, there’s been a widely held belief that iOS devices—such as iPhones—are virtually immune to phishing attacks, largely due…
As part of an ongoing international crackdown known as Operation PowerOFF, international law enforcement has seized over two dozen platforms…
Dec 12, 2024Ravie LakshmananWebsite Security / Vulnerability Malicious actors are exploiting a critical vulnerability in the Hunk Companion plugin for…
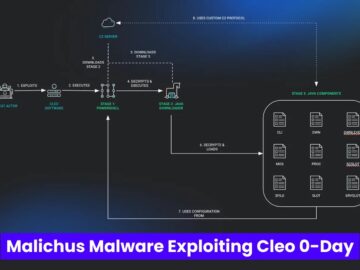
Threat actors are actively exploiting a critical zero-day vulnerability (CVE-2024-50623) in Cleo’s file transfer products Harmony, VLTrader, and LexiComis. The…
Cybersecurity has become one of the most high-stakes facets of business operations in the past few years. The chief information…
Deloitte denied its systems were hacked by Brain Cipher ransomware group Pierluigi Paganini December 09, 2024 Deloitte has responded to…
Law enforcement agencies worldwide have disrupted a holiday tradition of launching Distributed Denial-of-Service (DDoS) attacks in a major blow to…
GitLab announced the release of critical security patches for its Community Edition (CE) and Enterprise Edition (EE). The newly released…
Russia’s Secret Blizzard APT targets Ukraine with Kazuar backdoor Pierluigi Paganini December 12, 2024 Russia-linked APT group Secret Blizzard is using Amadey…
In a significant disruption, OpenAI’s popular AI chatbot, ChatGPT, experienced a global outage on Thursday morning, leaving millions of users…
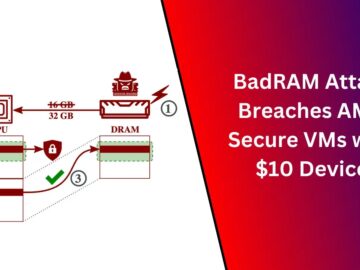
Researchers have uncovered a vulnerability that allows attackers to compromise AMD’s Secure Encrypted Virtualization (SEV) technology using a $10 device….
Years before the controversial Horizon system was introduced in 1999, subpostmasters who used a Post Office system known as Capture…