Author: Cybernoz
Since making Kerberos the default Windows authentication protocol in 2000, Microsoft has been working on eventually retiring NTLM, its less…
Cybersecurity researchers have discovered a novel surveillance program that’s suspected to be used by Chinese police departments as a lawful…
The Cybersecurity and Infrastructure Security Agency (CISA) has released seven new advisories highlighting critical vulnerabilities in widely used Industrial Control…
A critical security vulnerability (CVE-2024-49115) in Windows Remote Desktop Services (RDS) has been disclosed, potentially allowing hackers to execute arbitrary…
Researchers from Google have demonstrated a new generation of quantum computer, called Willow, which is able to run its random…
A significant security flaw in Apple’s iOS operating system has been uncovered, allowing malicious applications to access sensitive user data…
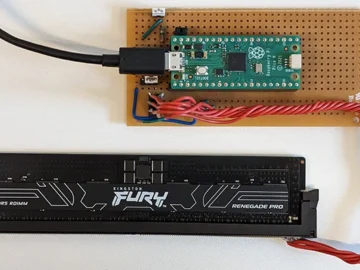
Cybersecurity researchers have identified a vulnerability (CVE-2024-21944, aka BadRAM) affecting ADM processors that can be triggered by rogue memory modules…
Chinese national charged for hacking thousands of Sophos firewalls Pierluigi Paganini December 11, 2024 The U.S. has charged a Chinese…
The cybersecurity firm Sichuan Silence and one of its employees, Guan Tianfeng, have been sanctioned by the Department of the…
Ivanti has issued critical software updates to address several severe vulnerabilities in its Cloud Services Application (CSA). These vulnerabilities tracked…
SUMMARY The new DCOM attack leverages Windows Installer service for stealthy backdoor deployment. Attack exploits the IMsiServer interface for remote…
Microsoft disclosed two significant vulnerabilities affecting its Office and Excel products as part of its December Patch Tuesday updates. These…