Author: Cybernoz
Dec 09, 2024Ravie LakshmananThreat Intelligence / Malware The threat actors linked to the Black Basta ransomware have been observed switching…
Electrica Group, a key player in the Romanian electricity distribution and supply market, is investigating a ransomware attack that was…
Just in time for the holiday season, Raspberry Pi has unveiled two highly anticipated products that are expected to be…
Cyber Defense Magazine Thought Leadership Interview with Nitesh Sinha, Founder and CEO of Sacumen and Praneeth Kudithipudi EVP Sales of…
Eight members of an international cybercrime network that stole millions of Euros from victims and set up Airbnb fraud centers were…
Cybercriminals leverage high-profile events, such as global sporting championships, by registering fake domains to launch phishing and scam attacks. Researchers…
Discover essential tips to secure your digital assets like crypto, NFTs, and tokens. Learn about wallet safety, avoiding phishing, 2FA,…
A critical vulnerability in OpenWrt’s firmware upgrade system has been recently unveieled by the security researcher RyotaK from Flatt Security…
In the rapidly evolving digital landscape, cybersecurity has emerged as a critical concern, particularly for the manufacturing sector. Recent data…
In recent years, we have seen cyberattacks targeting election infrastructure, with the aim of either influencing results or manipulating those…
Microsoft, in collaboration with the Institute of Science and Technology Australia and ETH Zurich, has announced the LLMail-Inject Challenge, a…
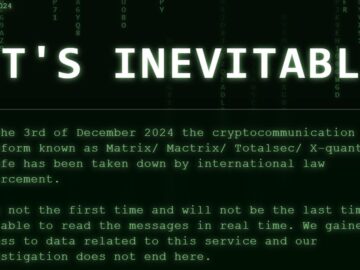
European law enforcement agencies have taken down yet another encrypted messaging service mainly used by criminals. The Matrix encrypted messaging…