Author: Cybernoz
In this Help Net Security interview, Tim Bramble, Director of Threat Detection and Response at OpenText, discusses how SOC teams…
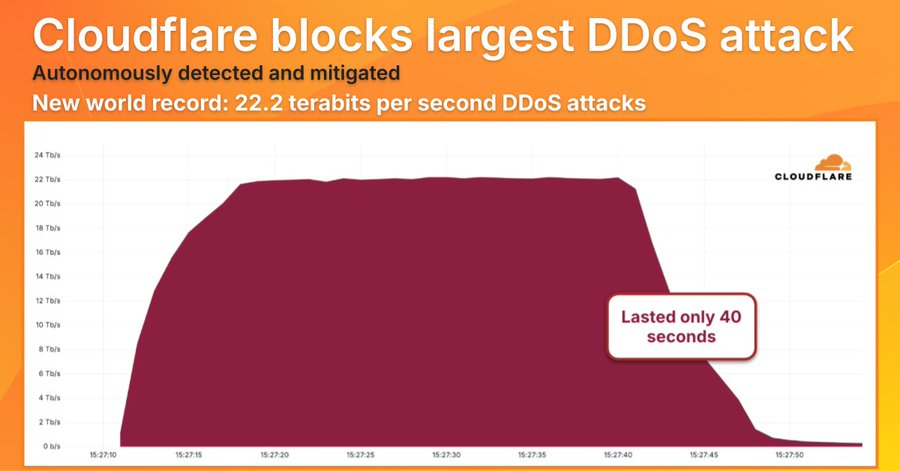
Cloudflare mitigates largest-ever DDoS attack at 22.2 Tbps Pierluigi Paganini September 24, 2025 Cloudflare blocked a new record-breaking DDoS attack…
Cybersecurity researchers at Zscaler ThreatLabz have identified a sophisticated new malware strain dubbed YiBackdoor, first detected in June 2025. This…
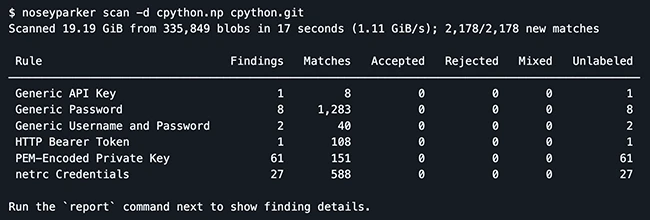
Nosey Parker is an open-source command-line tool that helps find secrets and sensitive information hidden in text files. It works…
In this Help Net Security video, David Hardoon, Global Head of AI Enablement at Standard Chartered, discusses the role of…
A firewall upgrade at Optus that caused Triple Zero calls to fail for 13 hours did not follow internal traffic…
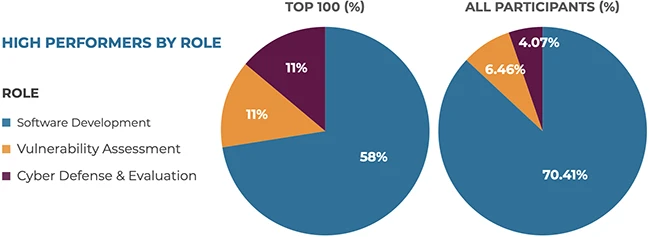
Software powers almost every part of business, which means attackers have more chances than ever to exploit insecure code. A…
Google has issued an urgent security update for its Chrome web browser to address three high-severity vulnerabilities that could allow…
Zloader, a sophisticated Zeus-based modular trojan that first emerged in 2015, has undergone a significant transformation from its original banking-focused…
Cyber security researchers have uncovered a sophisticated distributed denial-of-service (DDoS) operation that they say blurs the line between traditional malware…
Cybersecurity professionals are facing an unprecedented acceleration in threat actor capabilities as the average breakout time—the period from initial access…
A sophisticated malware campaign has emerged in the npm ecosystem, utilizing an innovative steganographic technique to conceal malicious code within…