Author: Cybernoz
A newly discovered phishing campaign is using fake Facebook copyright infringement notices to trick users into divulging their credentials, potentially…
Feb 07, 2025Ravie LakshmananFinancial Security / Regulatory Compliance India’s central bank, the Reserve Bank of India (RBI), said it’s introducing…
The number of advertised IT jobs dropped year-on-year in 2024, according to research by the Recruitment and Employment Federation (REC)….
The Taiwan government’s recent decision to implement a ban on the use of the DeepSeek artificial intelligence chatbot within its…
Cybercriminals are actively exploiting vulnerabilities in SimpleHelp Remote Monitoring and Management (RMM) software to infiltrate networks, create unauthorized administrator accounts,…
US-based construction, geospatial and transportation technology solutions provider Trimble has warned customers of its Cityworks product about a vulnerability that…
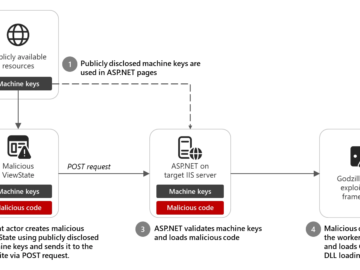
Attackers used a public ASP.NET machine to conduct ViewState code injection attacks Pierluigi Paganini February 07, 2025 Microsoft researchers warn…
The way we manage digital identity is fundamentally broken. The root of the problem lies in traditional, centralized identity models,…
A recent security incident has revealed that over 3,000 publicly disclosed ASP.NET machine keys were exploited by hackers to execute…
Splunk, a leader in data analytics and cybersecurity solutions, has introduced a groundbreaking proof-of-concept honeypot system named DECEIVE (DECeption with…
UK uses Richter Scale measurement for Cyber Attacks The United Kingdom has introduced a groundbreaking new method for assessing the…
As I write this, the front page of GitHub.com declares in big bold letters that this is “Where the world…