Author: Cybernoz
Amazon Web Services (AWS) unveiled a new service, AWS Security Incident Response, designed to help organizations manage security events efficiently….
Application Security Engineer TE Connectivity | USA | Remote – View job details As an Application Security Engineer, you will…
A proof-of-concept (PoC) exploit has been released for a critical zero-day vulnerability in the Windows Task Scheduler, identified as CVE-2024-49039….
With Sweet, customers can now unify detection and response for applications, workloads, and cloud infrastructure Sweet Security today announced the…
With Sweet, customers can now unify detection and response for applications, workloads, and cloud infrastructure Sweet Security today announced the…
New zero-day attack bypasses antivirus, sandboxes, and spam filters using corrupted files. Learn how ANY.RUN’s sandbox detects and combats these…
Richard Horne, the new CEO of the UK’s National Cyber Security Centre (NCSC) is today calling for “sustained vigilance in…
SUMMARY Rockstar 2FA Exposed: Trustwave uncovers Rockstar 2FA, a phishing-as-a-service (PhaaS) platform targeting Microsoft 365 accounts with advanced tools. 2FA…
Google undoubtedly dominates the desktop browser market, while Microsoft Edge has shown notable growth in recent times. However, Firefox continues…
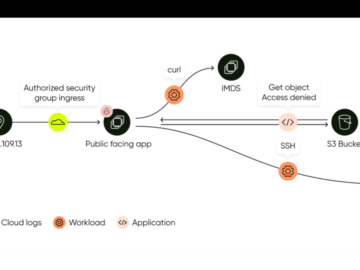
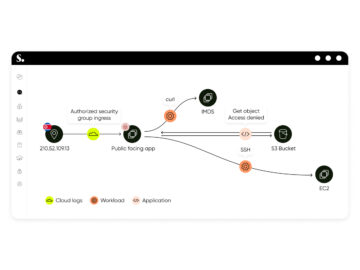
Tel Aviv, ISRAEL, December 3rd, 2024, CyberNewsWire Sweet Security Introduces Evolutionary Leap in Cloud Detection and Response, Releasing First Unified…
Tel Aviv, ISRAEL, December 3rd, 2024, CyberNewsWire Sweet Security Introduces Evolutionary Leap in Cloud Detection and Response, Releasing First Unified…
As artificial intelligence (AI) blurs the line between human and machine attackers, and quantum computing threatens to unravel encryption standards,…