Author: Cybernoz
With Sweet, customers can now unify detection and response for applications, workloads, and cloud infrastructure Sweet Security today announced the…
New zero-day attack bypasses antivirus, sandboxes, and spam filters using corrupted files. Learn how ANY.RUN’s sandbox detects and combats these…
Richard Horne, the new CEO of the UK’s National Cyber Security Centre (NCSC) is today calling for “sustained vigilance in…
SUMMARY Rockstar 2FA Exposed: Trustwave uncovers Rockstar 2FA, a phishing-as-a-service (PhaaS) platform targeting Microsoft 365 accounts with advanced tools. 2FA…
Google undoubtedly dominates the desktop browser market, while Microsoft Edge has shown notable growth in recent times. However, Firefox continues…
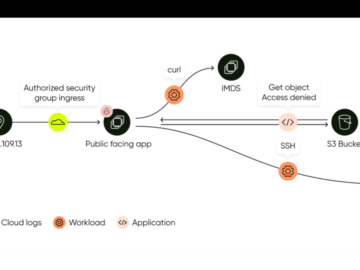
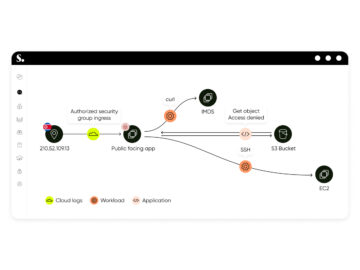
Tel Aviv, ISRAEL, December 3rd, 2024, CyberNewsWire Sweet Security Introduces Evolutionary Leap in Cloud Detection and Response, Releasing First Unified…
Tel Aviv, ISRAEL, December 3rd, 2024, CyberNewsWire Sweet Security Introduces Evolutionary Leap in Cloud Detection and Response, Releasing First Unified…
As artificial intelligence (AI) blurs the line between human and machine attackers, and quantum computing threatens to unravel encryption standards,…
South Korean police have arrested a CEO and five employees for manufacturing over 240,000 satellite receivers pre-loaded or later updated…
Russian authorities have sentenced the leader of the criminal group behind the now-closed dark web platform Hydra Market to life…
A novel phishing attack abuses Microsoft’s Word file recovery feature by sending corrupted Word documents as email attachments, allowing them…
SUMMARY Targeted Campaign: SmokeLoader malware attacks Taiwanese industries, including manufacturing, healthcare, and IT. Phishing Emails: The campaign uses phishing emails…