Author: Cybernoz
Amazon Web Services (AWS), the cloud computing division of Amazon Inc., has introduced a new Security Incident Response service designed…
The federal government has been asked to regulate “high-risk” uses of artificial intelligence as part of a raft of measures…
Imagine a world where artificial intelligence (AI) not only streamlines your daily tasks but also enhances your creativity. As we…
Tor Project needs 200 WebTunnel bridges more to bypass Russia’ censorship Pierluigi Paganini December 02, 2024 The Tor Project seeks…
Could 2025 be the year that reshapes cybersecurity in the financial services industry for good? With increasingly sophisticated cyber threats…
Malaysian minister Fahmi Fadzil has tabled two crucial pieces of legislation aimed at addressing the rising threats of online harassment…
SUMMARY: Crypto losses in November 2024 totalled $71 million, marking a 79% decrease from the same month in 2023. DeFi…
Everything in IT gets commoditised eventually, according to Terren Peterson, vice-president of engineering at Capital One. Having worked at the…
Google undoubtedly dominates the desktop browser market, while Microsoft Edge has shown notable growth in recent times. However, Firefox continues…
Amazon Web Services (AWS) has signed a multi-year partnership to draw on the artificial intelligence (AI) expertise of US-based Orbital…
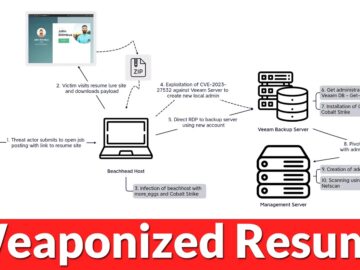
A sophisticated cyber attack was detected in March 2024, revealing a complex intrusion that began with a weaponized resume and…
Hewlett Packard Enterprise (HPE) has issued an urgent security bulletin addressing a critical vulnerability in its IceWall product line. Identified…