Author: Cybernoz
Researchers regularly see malicious ads in search results representing themselves as coming from legitimate businesses and organizations. Whether it’s a…
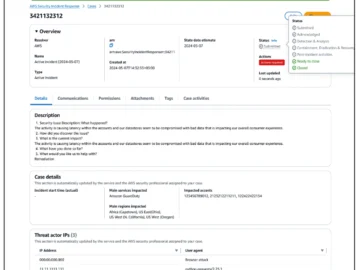
Amazon Web Services (AWS) has launched a new service to help organizations prepare for and recover from ransomware attacks, account…
Dec 02, 2024The Hacker NewsAI Security / Data Protection Artificial Intelligence (AI) is no longer a far-off dream—it’s here, changing…
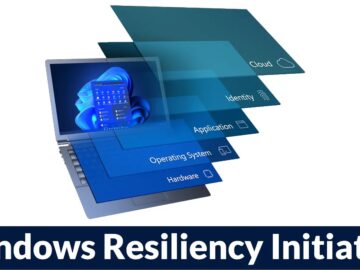
Microsoft has announced its Windows Resiliency Initiative, a comprehensive strategy aimed at fortifying Windows against emerging threats, with a particular…
Interpol: Operation HAECHI-V led to more than 5,500 suspects arrested Pierluigi Paganini December 02, 2024 International law enforcement operation Operation…
A novel phishing attack abuses Microsoft’s Word file recovery feature by sending corrupted Word documents as email attachments, allowing them…
IBM disclosed multiple critical vulnerabilities affecting its Security Verify Access Appliance, potentially exposing users to severe security risks. The vulnerabilities…
Recent research uncovered a novel crypto-jacking attack targeting the Python Package Index (PyPI), where malicious actors uploaded a legitimate-seeming cryptocurrency…
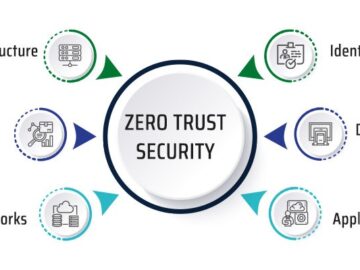
Zero trust security takes an “never trust, always verify” approach to access control. Access is only granted once an individual’s…
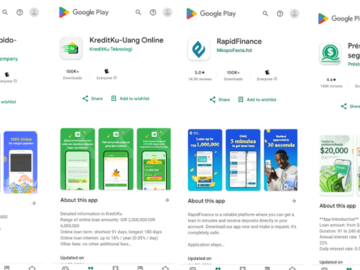
Dec 02, 2024Ravie LakshmananMobile Security / Financial Fraud Over a dozen malicious Android apps identified on the Google Play Store…
Google Chrome’s upcoming feature uses AI to provide a summary of reviews from independent websites about the store or website…
A high-severity security vulnerability has been recently disclosed by Hewlett Packard Enterprise (HPE) in its IceWall products that could potentially…