Author: Cybernoz
North Korean threat actors target software developers with weaponized Javascript projects that include BeaverTail malware deployed via NPM packages. It…
Social media platforms will have to start verifying the age of Australian users by this time next year but cannot…
A critical security flaw has been discovered in Zabbix, the popular open-source monitoring solution, potentially allowing attackers to gain full…
Nov 28, 2024The Hacker NewsCloud Security / Threat Detection Serverless environments, leveraging services such as AWS Lambda, offer incredible benefits…
Fujitsu has parted company with its UK head of charitable partnerships and restructured how it engages with charities, at a…
Hewlett Packard Enterprise (HPE) has disclosed multiple high-severity vulnerabilities in its Insight Remote Support (IRS) software, potentially allowing attackers to…
The xattr command in Unix-like systems allows for the embedding of hidden metadata within files, similar to Windows ADS, known…
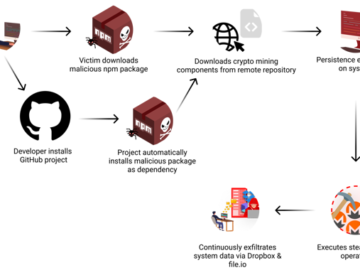
Nov 28, 2024Ravie LakshmananSoftware Security / Data Breach Cybersecurity researchers have discovered a software supply chain attack that has remained…
In today’s dynamic threat landscape, security leaders are under constant pressure to make informed choices about which solutions and strategies…
The Australian government has passed the new Cyber Security Act, which was recently approved by Parliament. One of the most…
Major UK healthcare provider Wirral University Teaching Hospital (WUTH), part of the NHS Foundation Trust, has suffered a cyberattack that caused…
A series of vulnerabilities have been identified, posing significant risks to the system’s security. These vulnerabilities could allow attackers to…