Author: Cybernoz
Law enforcement agencies in Africa arrested as part of ‘Operation Serengeti’ more than a thousand individuals suspected of being involved in…
Cryptocurrencies are a relatively new asset class, and over the years, they have continued to be the subject of scrutiny…
Aqua Nautilus researchers have discovered a campaign powering a series of large-scale DDoS attacks launched by Matrix, which could be…
The Nuclear Decommissioning Authority (NDA), the quasi-government body that serves to wind-up and make safe the UK’s oldest nuclear industry…
In a House of Lords debate looking at large language models and generative artificial intelligence (GenAI), Tina Stowell, chair of…
Russian-aligned hacking group RomCom has been discovered exploiting two critical zero-day vulnerabilities affecting Mozilla Firefox and Windows systems in a…
Earth Estries, a Chinese APT group, has been actively targeting critical sectors like telecommunications and government entities since 2023. They…
A ransomware attack on the systems of Blue Yonder, a specialist supply chain management software provider based in the US,…
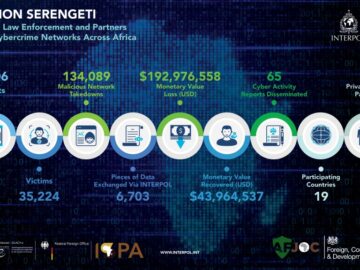
An unprecedented crackdown on cybercrime across Africa has resulted in the arrest of 1,006 suspects and the dismantling of 134,089…
Over the years, we’ve witnessed a range of cyberattacks targeting everything from personal computers and smart devices to the increasingly…
Researchers have discovered vulnerabilities in the update process of Palo Alto Networks (CVE-2024-5921) and SonicWall (CVE-2024-29014) corporate VPN clients that…
In today’s dynamic threat landscape, security leaders are under constant pressure to make informed choices about which solutions and strategies…