Author: Cybernoz
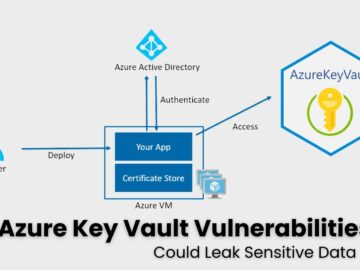
A detailed walkthrough demonstrates how attackers can manipulate Azure Key Vault’s access policies after compromising Entra ID (formerly Azure AD)…
A recently discovered Cross-site Scripting (XSS) vulnerability, CVE-2024-57514, affecting the TP-Link Archer A20 v3 Router has raised security concerns among…
In this Help Net Security interview, James Mirfin, SVP and Head of Risk and Identity Solutions at Visa, discusses key…
Jan 29, 2025Ravie LakshmananCyber Espionage / Threat Intelligence The advanced persistent threat (APT) group known as UAC-0063 has been observed…
The rapid adoption of artificial intelligence (AI) has triggered both excitement and unease in the cybersecurity community. On one hand,…
The rapid adoption of artificial intelligence (AI) has triggered both excitement and unease in the cybersecurity community. On one hand,…
The HackerOnesie instantly became famous the day it was introduced in 2017. Although it has been known to carry magical…
Cloudflare revealed how its data pipeline has achieved unprecedented scalability, processing up to 706 million events per second as of…
The number of US data compromises in 2024 (3,158) decreased 1% compared to 2023 (3,202), 44 events away from tying…
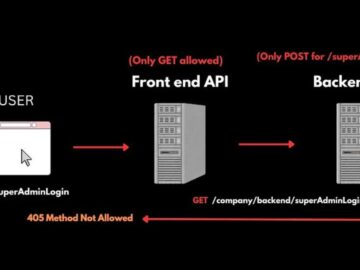
Cybersecurity researchers have exposed critical vulnerabilities in a telecom network that allowed unauthorized access to sensitive data and control over…
Ransomware attacks are disrupting and undermining business operations and draining revenue streams, according to Illumio. Findings from the study reveal…
The program began in 2021 as an internal resource for engineers to be mentors and mentees. Mentors build their leadership…