Author: Cybernoz
Microsoft has released the optional KB5046714 Preview cumulative update for Windows 10 22H2 with six bug fixes, including a fix…
QNAP has pulled a recently released firmware update after widespread customer reports that it’s breaking connectivity and, in some cases,…
Ahead of the the 2024 US elections, the US intelligence community and law enforcement were on high alert and ready…
Russian state hackers APT28 (Fancy Bear/Forest Blizzard/Sofacy) breached a U.S. company through its enterprise WiFi network while being thousands of…
The Shadowserver Foundation reports over 2,000 Palo Alto Networks firewalls have been hacked via two zero-day vulnerabilities: CVE-2024-0012 & CVE-2024-9474,…
Microsoft announced today that its controversial AI-powered Recall feature is finally rolling out to Windows Insiders in the Dev Channel…
Nov 22, 2024Ravie LakshmananCyber Espionage / Malware A China-linked nation-state group called TAG-112 compromised Tibetan media and university websites in…
Meta provided insight this week into the company’s efforts in taking down more than 2 million accounts that were connected…
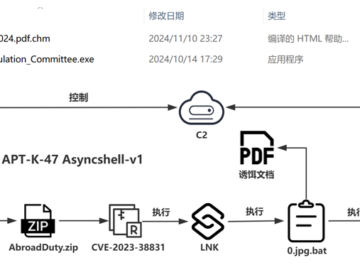
Nov 22, 2024Ravie LakshmananCyber Attack / Malware The threat actor known as Mysterious Elephant has been observed using an advanced…
Learn how to prevent payment fraud with effective fraud detection, online prevention solutions, and secure payment orchestration strategies. The Basics…
An independent inquiry into the mobile browser market has recommended that the Competition and Markets Authority (CMA) consider investigating Apple…
73% of globally exposed ICS systems are in the US and Europe, with the US leading at 38%. Vulnerabilities in…