Author: Cybernoz
Kaspersky’s Global Research and Analysis Team (GReAT) has recently uncovered a sophisticated supply chain attack targeting the Python Package Index…
Nov 21, 2024Ravie LakshmananArtificial Intelligence / Software Security Google has revealed that its AI-powered fuzzing tool, OSS-Fuzz, has been used…
Decade-old local privilege escalation bugs impacts Ubuntu needrestart package Pierluigi Paganini November 21, 2024 Decade-old flaws in the needrestart package…
A high-severity security vulnerability in Kubernetes has been discovered, potentially allowing attackers to execute arbitrary commands beyond container boundaries. The…
The unfortunate reality is that – for the safety of the people attending – security measures are now an absolute…
SailPoint Technologies, Inc., a recognized leader in enterprise identity security, has unveiled an ambitious new vision for the future of…
The CWE list of the 25 most dangerous software weaknesses demonstrates the currently most common and impactful software flaws. Identifying…
The U.S. law enforcement has unsealed criminal charges against five individuals involved in a large-scale phishing scheme targeting employees at…
A critical vulnerability in macOS WorkflowKit, the framework underpinning Apple’s Shortcuts app, has been disclosed. This vulnerability allows malicious applications…
Helldown, a new ransomware group, actively exploits vulnerabilities to breach networks, as since August 2024, they have compromised 28 victims,…
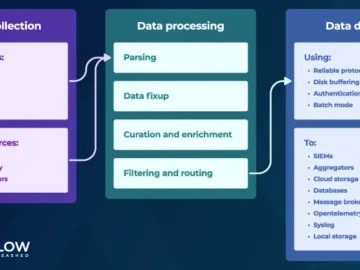
AxoSyslog is a syslog-ng fork, created and maintained by the original creator of syslog-ng, Balazs Scheidler, and his team. “We…
Threat hunters are warning about an updated version of the Python-based NodeStealer that’s now equipped to extract more information from…