Author: Cybernoz
A significant security vulnerability, designated CVE-2025-21613, has been discovered in the go-git library, used for Git version control in pure…
Millions of devices, including home routers, VPN servers, and CDNs are vulnerable to exploitation due to critical flaws in common…
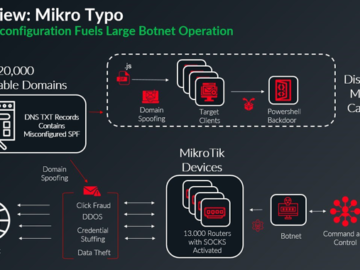
Jan 21, 2025Ravie LakshmananEmail Security / Botnet A global network of about 13,000 hijacked Mikrotik routers has been employed as…
Mozilla Firefox and Thunderbird users are facing a series of high-severity vulnerabilities that could leave systems open to exploitation. The…
With the advent of Zero Trust architecture, where the principle of “never trust, always verify” prevails, the importance of comprehensive…
The Gootloader malware family employs sophisticated social engineering tactics to infiltrate computers. By leveraging compromised legitimate WordPress websites, Gootloader’s operators…
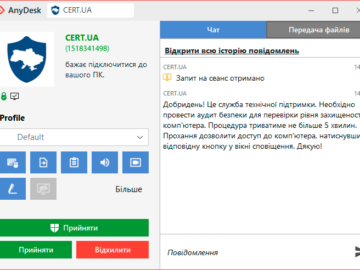
CERT-UA warned of scammers impersonating the agency using fake AnyDesk requests Pierluigi Paganini January 21, 2025 CERT-UA warned of scammers…
A security vulnerability has been identified in Brave Browser, potentially allowing malicious websites to masquerade as trusted ones during file…
A former analyst working for the U.S. Central Intelligence Agency (CIA) pleaded guilty to transmitting top secret National Defense Information…
A recent phishing campaign has targeted customers of SBI Bank through a deceptive message circulating in WhatsApp groups. The message…
The latest spending forecast from Gartner predicts that more than twice as much is being spent on AI-optimised servers compared…
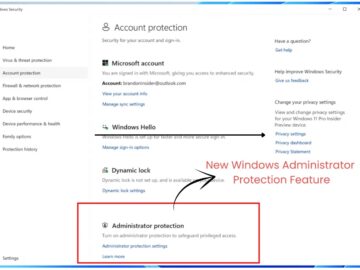
Microsoft has unveiled a groundbreaking security feature called Administrator Protection, now available to Windows Insiders in the Canary Channel with…