Author: Cybernoz
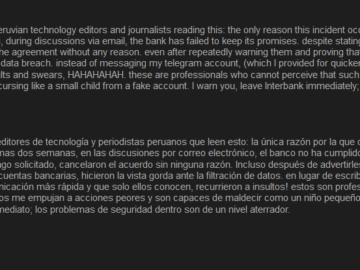
Threat actor says Interbank refused to pay the ransom after a two-week negotiation Pierluigi Paganini October 31, 2024 Peruvian Interbank…
Cost savings and business benefits were quantified in “The Total Economic Impact™ of Cynet All-in-One Security,” a commissioned study conducted…
Cybersecurity researchers uncovered the “Xiū gǒu” phishing kit targeting users in the UK, US, Spain, Australia, and Japan. Active across…
A cyber threat group known as 888 has made headlines by claiming it has successfully infiltrated the servers of International…
Oct 31, 2024Ravie LakshmananSpyware / Mobile Security Cybersecurity researchers have discovered an improved version of an Apple iOS spyware called…
qBittorrent has addressed a remote code execution flaw caused by the failure to validate SSL/TLS certificates in the application’s DownloadManager,…
Carrying out malware analysis might seem like a lengthy and complex task, but with the right tools and practices, it…
The issue of GitHub data protection is increasingly discussed among developers on platforms like Reddit, X, and HackerNews. This year…
Oct 31, 2024Ravie LakshmananCryptocurrency / Software Development LottieFiles has revealed that its npm package “lottie-player” was compromised as part of…
Microsoft has fixed a known issue that prevents some apps launched from non-admin accounts from starting on Windows 10 22H2…
Sophos conducted defensive and counter-offensive operation over the last five years with multiple interlinked nation-state adversaries based in China targeting…
A phishing campaign dubbed ‘Phish n’ Ships’ has been underway since at least 2019, infecting over a thousand legitimate online…