Author: Cybernoz
On the second day of Pwn2Own Ireland 2024, competing white hat hackers showcased an impressive 51 zero-day vulnerabilities, earning a…
When it comes to protecting your business from increasingly sophisticated cyber threats, a Managed Security Information and Event Management (SIEM)…
24 Oct In a Cloudy World, On-Premises Still Might be The Way To Go Posted at 10:11h in Blogs by…
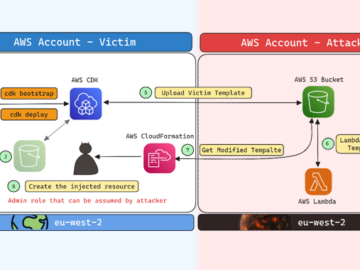
Cybersecurity researchers have disclosed a security flaw impacting Amazon Web Services (AWS) Cloud Development Kit (CDK) that could have resulted…
A critical vulnerability has been identified in the Cisco Adaptive Security Appliance (ASA) Software, posing a significant security risk to…
A cybersecurity researcher discovered a massive data leak exposing over 115,000 sensitive documents associated with the UN Trust Fund to…
Oct 24, 2024Ravie LakshmananVulnerability / Network Security Cisco on Wednesday said it has released updates to address an actively exploited…
The file upload vulnerability type is as broad in scope as the number of different file types. These vulnerabilities are…
Wallarm’s Security Edge is setting a new standard in API security—far beyond the reach of traditional Content Delivery Networks (CDNs)….
The U.S. Department of State’s Rewards for Justice program has launched a major initiative offering up to $10 million for…
Cybersecurity compliance is undergoing a massive shift, with regulatory frameworks rapidly introducing more complex rules, stricter enforcement, and tougher penalties…
With global cybercrime damage projected to reach $10.5 trillion annually by 2025, according to Cybersecurity Ventures, the international tech community is…