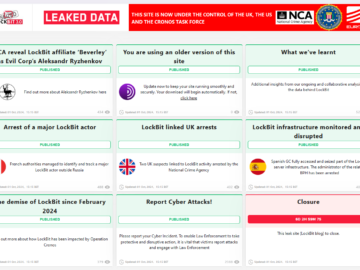
Author: Cybernoz
The federal government has created a “review framework” to measure the national security and supply chain security risks that technology…
The NBN needs to remain “under the control of the elected government” as a national security measure, according to the…
GenesisCare, a cancer care provider, has named former Healthscope CIO Brett Winn as its chief information and digital officer. Image…
Australia’s ‘Big 4’ banks – CBA, NAB, ANZ and Westpac – flagged and/or “exited” thousands of bank accounts in the…
Security Affairs newsletter Round 503 by Pierluigi Paganini – INTERNATIONAL EDITION Pierluigi Paganini December 22, 2024 A new round of…
Welcome to this week’s Cyber Security Newsletter, where we explore the latest advancements and important updates in the field of…
US charged Dual Russian and Israeli National as LockBit Ransomware developer Pierluigi Paganini December 22, 2024 US authorities charged a…
Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: MUT-1244 targeting security researchers, red…
Almost every single organisation, large or small, is acutely aware of the need to implement robust security measures. However, this…
New Board Members Include Top Leaders in Tech, Scientific Communities Charlottesville, VA (12/18/2024) — RIIG, an AI driven risk intelligence…
A new phishing-as-a-service (PaaS) platform called “FlowerStorm” has emerged, targeting Microsoft 365 users. This platform has quickly gained traction following…
A senate bid to access key documents relating to PsiQuantum’s $940m funding deal from government has drawn a blank, with…