Author: Cybernoz
Certificate-Based Authentication (CBA) is a robust security mechanism that has been a cornerstone in high-security environments for decades. It leverages…
The Cybersecurity and Infrastructure Security Agency (CISA) has recently added three vulnerabilities to its Known Exploited Vulnerabilities (KEV) Catalog, emphasizing…
GhostStrike is an open-source, advanced cybersecurity tool tailored for ethical hacking and Red Team operations. It incorporates cutting-edge techniques, including…
A recent cyberattack has highlighted the growing threat of North Korean operatives infiltrating Western companies by posing as remote IT…
In this Help Net Security interview, Mick Baccio, Global Security Advisor at Splunk SURGe, discusses the far-reaching implications of the…
While businesses increasingly rely on SaaS tools, many leaders are not fully confident in their ability to safeguard their data,…
Beyond Bank has boosted its call centre experience and digital capabilities, leading to a customer satisfaction uplift of 92 percent. …
The tech regulatory landscape is constantly evolving, with the imminent Network and Information Security 2 Directive, more widely known as…
Iranian hackers are breaching critical infrastructure organizations to collect credentials and network data that can be sold on cybercriminal forums…
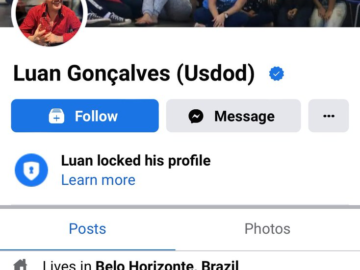
Brazilian police have arrested the hacker known as USDoD, responsible for high-profile breaches including the FBI’s InfraGard and National Public…
Brazil’s Polícia Federal arrested the notorious hacker USDoD Pierluigi Paganini October 16, 2024 Brazil’s Polícia Federal has arrested hacker USDoD,…
A notorious hacker named USDoD, who is linked to the National Public Data and InfraGard breaches, has been arrested by…