Author: Cybernoz
Amazon has seen massive adoption of passkeys since the company quietly rolled them out a year ago, announcing today that…
A joint report by AhnLab Security Emergency response Center (ASEC) and the National Cyber Security Center (NCSC) has revealed a…
In today’s rapidly evolving digital landscape, organizations are increasingly reliant on complex networks of identities to power their operations. From…
Microsoft’s customers are under constant cyber assault, facing millions of attacks daily from various threat actors as nation-states and cybercrime…
Over the past five years, cybersecurity budgets have witnessed a steady and substantial increase. Global spending on cybersecurity products and…
Cybersecurity threats have become increasingly prevalent and sophisticated in recent years, posing significant risks to businesses of all sizes. In…
Oct 16, 2024Ravie LakshmananZero-Day / Windows Security The North Korean threat actor known as ScarCruft has been linked to the…
The Android boot chain initiates with the “Boot ROM,” which initializes the “bootloader.” The bootloader then loads the kernel, which is…
EDRSilencer, a red team tool, interferes with EDR solutions by blocking network communication for associated processes using the WFP, which…
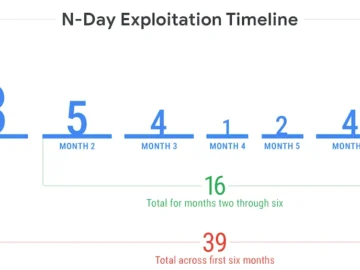
A new report from Mandiant reveals that the average time-to-exploit vulnerabilities before or after a patch is released has plunged…
Mozilla has announced a security fix for its Firefox browser which also impacts the closely related Tor Browser. The new…
Oct 16, 2024The Hacker NewsArtificial Intelligence / Cybercrime AI from the attacker’s perspective: See how cybercriminals are leveraging AI and…