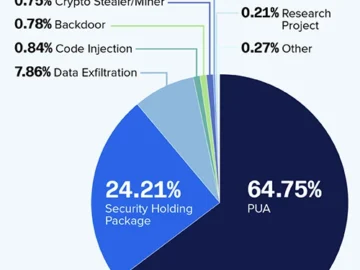
Author: Cybernoz
Containers are the fastest growing – and weakest cybersecurity link – in software supply chains, according to NetRise. Companies are…
Sonatype’s 2024 Open Source Malware Threat Report reveals that the number of malicious packages has surpassed 778,500 since tracking began…
In this Help Net Security interview, Allison Ritter, Head of Cyber Experiential Exercising at Cyberbit, shares her insights on the…
Dec 11, 2024Ravie LakshmananVulnerability / Network Security Ivanti has released security updates to address multiple critical flaws in its Cloud…
Google has released a critical security update for its Chrome browser, addressing three high-severity vulnerabilities that could potentially expose users…
More than a decade after the advent of the 3D-printed gun as an icon of libertarianism and a gun control…
Microsoft today released updates to plug at least 70 security holes in Windows and Windows software, including one vulnerability that…
U.S. CISA adds Microsoft Windows CLFS driver flaw to its Known Exploited Vulnerabilities catalog Pierluigi Paganini December 11, 2024 U.S. Cybersecurity…
Cyble researchers have detected a new campaign targeting Russia by the hacktivist group Head Mare that uses a disguised LNK…
Microsoft December 2024 Patch Tuesday addressed actively exploited zero-day Pierluigi Paganini December 10, 2024 Microsoft December 2024 Patch Tuesday security…
Microsoft has issued fixes for 71 new Common Vulnerabilities and Exposures (CVEs) to mark the final Patch Tuesday of 2025,…
U.S. Senator Ron Wyden of Oregon announced a new bill to secure the networks of American telecommunications companies breached by…