Author: Cybernoz
Arriving on 17th October this year, NIS 2 is the EU’s most stringent cybersecurity Directive so far. Your level of cybersecurity…
Rich Corbridge, the chief digital and information officer at the Department for Work and Pensions (DWP), is leaving his role…
DMARC is an email authentication protocol that helps domain owners protect against unauthorized use like “email spoofing” and “phishing attacks.”…
The Awaken Likho APT group launched a new campaign in June of 2024 with the intention of targeting Russian government…
San Francisco, CA, October 8th, 2024, CyberNewsWire Partnership aims to help businesses eliminate vulnerable attack surfaces and provide a more…
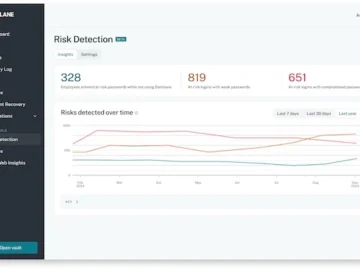
Dashlane launched Credential Risk Detection, a solution that continuously monitors and detects at-risk credential activity in real-time across the workforce,…
Qualcomm fixed a zero-day exploited limited, targeted attacks Pierluigi Paganini October 08, 2024 Qualcomm warns of 20 flaws in its…
Japanese tech giant Casio has suffered a cyberattack after an unauthorized actor accessed its networks on October 5, causing system…
DNS tunneling is a hacking technique that hides information by taking advantage of the DNS protocol. This attack enables threat…
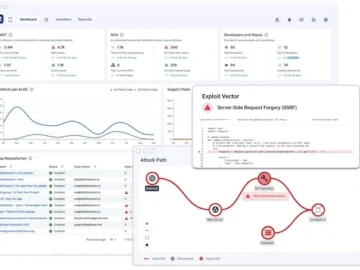
Data Theorem launched Code Secure, the latest evolution in application security designed to protect the software supply chain from code…
It is a tale almost as old as time: users click download, install, and accept as they adopt new software…
One of the recurring questions we hear from network security leaders is “why aren’t our security policies optimized?” The answer,…