Author: Cybernoz
The percentage of Android vulnerabilities caused by memory safety issues has dropped from 76% in 2019 to only 24% in…
An exposed database at background check company MC2 Data apparently leaked the data of more than 100 million Americans. MC2,…
Australian Red Cross has rolled out a series of AI use cases following the completion of its foundational “digital spine”….
Meta announced that it’s ending its direct peering relationship with Deutsche Telekom following a court’s ruling earlier this year that…
Dell faces its third data leak in a week as hacker “grep” continues targeting the tech giant. Sensitive internal files,…
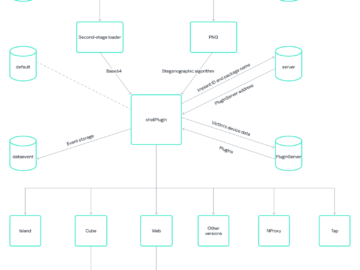
New variant of Necro Trojan infected more than 11 million devices Pierluigi Paganini September 25, 2024 Experts warn of Necro…
European digital rights group NOYB (None Of Your Business) has filed a privacy complaint with the Austrian data protection watchdog…
The highly anticipated 2025 Cybersecurity Excellence Awards are now open for nominations, honoring achievements and celebrating innovation, leadership, and excellence…
UEEx enhances user security with new compensation policies addressing abnormal market volatility and asset protection. Users can now recover losses…
Sep 25, 2024Ravie LakshmananSecure Coding / Mobile Security Google has revealed that its transition to memory-safe languages such as Rust…
CISA warned today of threat actors trying to breach critical infrastructure networks by targeting Internet-exposed industrial devices using “unsophisticated” methods…
Safebrowsing utilizes a cloud-based virtual browser environment to analyze potentially risky websites. This isolated environment protects the local system from…