Author: Cybernoz
A newly discovered vulnerability in Apache Tomcat, identified as CVE-2024-38286, has raised significant concerns among cybersecurity experts. This flaw allows…
Sep 24, 2024Ravie LakshmananMobile Security / Cybercrime Cybersecurity researchers have discovered a new version of an Android banking trojan called…
China’s Ministry of State Security (MSS) has identified a hacking group known as Anonymous 64, claiming it is an “internet…
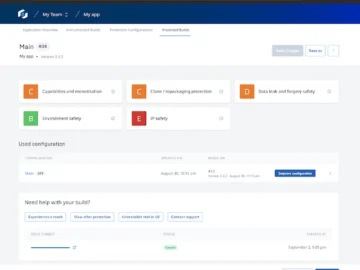
Rob Samuels | 24 September 2024 at 10:01 UTC AppSec teams face a wide range of challenges when securing their…
Telegram will start handing over the IP addresses and phone numbers of users who violate their Terms of Service “to…
GeoServer is an open-source server written in Java that enables users to share, process, and edit geospatial data. It supports…
Guardsquare announced an innovative, guided approach to mobile application security that empowers teams to achieve the highest level of protection…
A critical unauthenticated Remote Code Execution (RCE) vulnerability has been discovered, impacting all GNU/Linux systems. As per agreements with developers,…
The UK government has announced a new collaboration with the US government and the Canadian government. This partnership aims to…
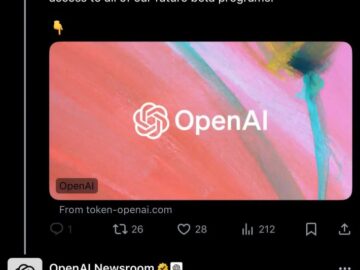
An official OpenAI account on X (formerly Twitter) was compromised on Monday evening, leading to the dissemination of a cryptocurrency…
Cisco disclosed a critical vulnerability identified as CVE-2024-20439, affecting its Smart Licensing Utility. An independent researcher discovered this vulnerability through…
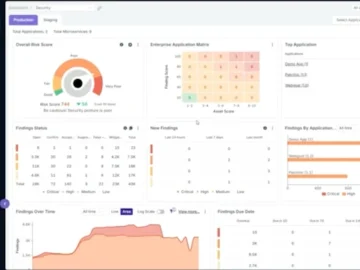
ArmorCode announced the expansion of its platform with the launch of two new modules for Penetration Testing Management and Exceptions…